Top Malware Anti-Analysis Coverage

Introduction:
Threat actors and malware authors use various anti-analysis techniques to keep initial access, execution, persistence, privilege escalation, credential access, lateral movement, command and control, and exfiltration of data hidden from the reverse engineers that try to peer inside their code. Usually this makes post-detection analysis more difficult. The malicious binaries below exhibit evasive behaviors which aim to detect or disrupt the analysis in a virtual machine or in your favorite debugger.
SonicWall Capture Labs Threat Research Team will present anti-debugging techniques and main concepts that cover a variety of top malware categories in today's malware. In anti-debugging, malware detects debuggers by searching for known indicators or artifacts used to implement core debugger functionalities, such as tracing, breakpoints, and hooking.
In this lower section, we cover only anti-debugging techniques used in the top malware families we have categorized below enabling us to present an analysis on the real state of evasion techniques in use by malware today. This is by no means a comprehensive catalog of known anti-debugging techniques used by the Windows API:
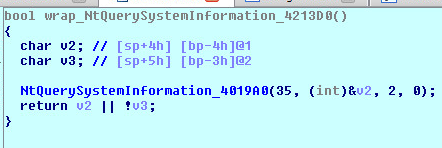
NtQuerySystemInformation:
NtQuerySystemInformation() function call of the ntdll.dll can be used with the undocumented SystemKernelDebuggerInformation as a SystemInformationClass parameter to detect the presence of a debugger. The result is stored in the buffer pointed by the SystemInformation parameter that has 2 bytes representing two flags. Each one with 8 bits (LSB KdDebuggerEnabled and MSB KdDebuggerNotPresent). KdDebuggerNotPresent is FALSE if a debugger is present.
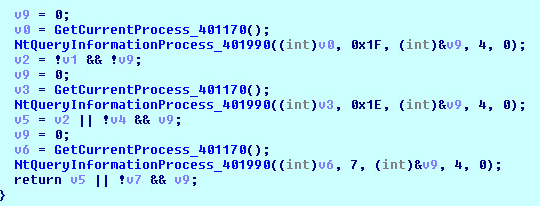
NtQueryInformationProcess:
NtQueryInformationProcess() used with ProcessDebugPort as a ProcessInformationClass parameter will set (-1)0xffffffff in the ProcessInformation parameter if a process is being debugged.
NtQueryInformationProcess() used with ProcessDebugObjectHandle as a ProcessInformationClass parameter to query for the debug object handle.
NtQueryInformationProcess() used with ProcessDebugFlags as a ProcessInformationClass parameter to set the inverse of EPROCESS->NoDebugInherit bit in the ProcessInformation parameter.
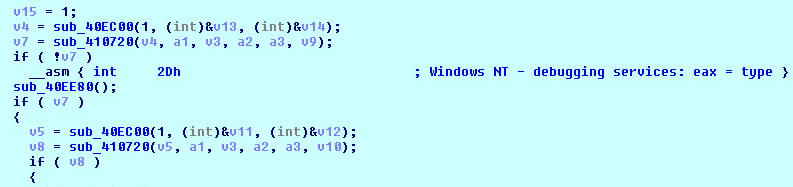
Windows Debugging Services:
asm { int 2dh }, is the interface for the Win32 kernel and provides kernel debugging services to user level debuggers and remote debuggers such as IMM, Kd and WinDbg.
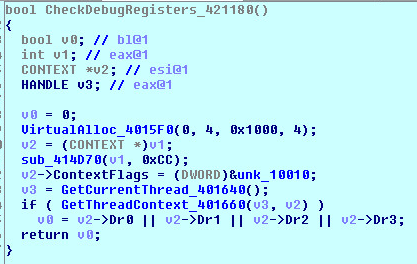
Hardware Breakpoints:
When an exception occurs, windows creates a context structure to pass to the exception handler. This structure will contain the values of the debug registers. The debug registers will contain values that will reveal the presence of a debugger. Another way includes using GetCurrentThread() and GetThreadContext() then testing the debug registers for values.
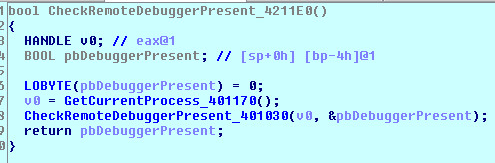
CheckRemoteDebuggerPresent:
CheckRemoteDebuggerPresent() is a kernel32.dll function that sets (-1)0xffffffff in the DebuggerPresent parameter if a debugger is present. Internally, it also uses NtQueryInformationProcess() with ProcessDebugPort as a ProcessInformationClass parameter.
Instruction Counting:
An exception handler is registered to deal with the EXCEPTION_SINGLE_STEP(0x80000004) exception. This will include the use of other Win32 APIs such as GetThreadContext(). The handler will simply count how many times it was reached and then change EIP to point to a new instruction and resume execution.
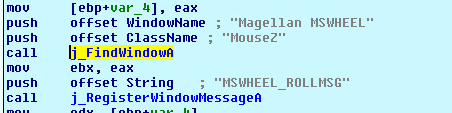
Find Window:
FindWindow() function can be used to find opened debuggers using both parameters, lpClassName and lpWindowName. Example: lpClassName: "OLLYDBG" or lpWindowName: "IDA".
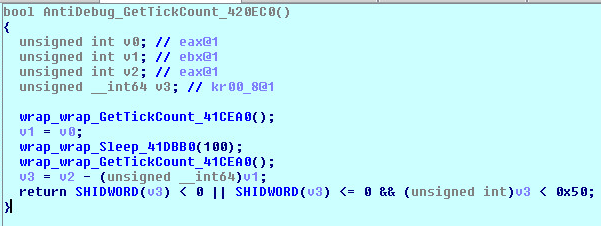
Execution Timing:
When a debugger is present, the time elapsed between instructions are measured. RDTSC assembly instruction is a very popular anti-debugging technique. However, others are also used such as RDPMC, RDMSR, GetTickCount(), GetLocalTime(), GetSystemTime(), and QueryPerformanceCounter().
Malware Family Coverage:
Botnet - (Pushdo):
- 19b37c17146d9b365529ffc8cc77627e6745ebc1c729c5238256c73c90da51ce
- 60c3a69e1605ae687d87b25d4b365764b429cb3b9a737ce54a25b26e8c7925ea
- bc5b8591c1431205e91684b7342b421e1dee6cc48dcf1f979e7b77902357aff5
- c5a1fe4b4efb6f82f52650a74d26ebf6e9b8bff44159ac950ad853c90cc5e4b1
Fileless - (Kovter):
- 63b3ccca49e9725f9d23f687aaf49670d7dc3911a9861ef6d5cbf0563daf0c2e
- 87a03fb02bd6064e26bf0bd10e5ec9e91680aa84b8f22b7950fb4478b80756aca
- ce2632cb0d044d1ded7bbb8e6641c42068ce8e25fe0bc236265003510a6eafbd
- f4c13bf9c10f6182d395842155aefff1383f9e3c9e9f9033f0cb865c79256587
Cryptojack - (Coinminer):
- a5af55d5e2e8c2d493f86c135832d306f4f568ea6749c2d6ff24ad622455c512
- ac4767ea7f70cc68c6ee85a87684006db0079d24e2a685c98873bb8b02746890
- feb251419cc220062e65609efd81c9eb307f61ac5cd36fd9aceec0bc419e008c
Ransomware - (Cerber):
- 327a9503b5b5d09669d2e516a0b0dbf53266b06c269616b22d9a66e898aaa4f2
- 563c47b15c78b68bd41db35a2af9fea77bc679cfa446a4fdc0400ef4e99f5a5b
- 723584a72cb469401489b455f238cfa77f92e16e2861e72b7a39718fd56fb9da
- 55346262aff4b260ab8a9e44186682c1374dffa953a42e2b01731ac697d59636
RAT - (Ghost):
- b0144595eea1790d235b8b4e1885929f48102cef899632439f2cfe4b837870a2
Spyware - (Lokibot):
- 534673bc3b061309221efc082d02927bf32f000d8985767e861d1b11a3b03057
- 38361585de3fa6b8793bbcb608aa79dbf25be083de61e888e4f71801ee2fab02
- c72cde7d189526c5bcdd80bc16e8cd7eee1e976465cb7793f4c2e7c684c7df7d
- facd430e4674fd773c5b3affd6130ca96917cdd59be537bde38b072e275ec2ad
Trojan - (agentTesla):
- 719865cf1608e2f8e0e4395ffff1ec34a517fddb099dd9ceb39c3398d2cd9797
- ba617f6635ce2caf19a9d5bb05a667fa7085aa7ee999148a5d2faaa1ac2df6bd
- e313e7310ccd7f9b7998b02de559097ec1190054ee2949421a6187b1feb26e95
- fd056b98472911f456cd1a5812b7a347f6f359a8c79ec4cce0bd51850528b932
Virus - (Ramnit):
- c9ef1e01e8659dc0592551ed6ed0d7f83e9977219e57eafce3a27c5208763836
SonicWall, GAV Cloud, provides protection as follows:
- 4db9ac02052fcd3dc4f018b759702fac Agent.FL (Trojan)
- ac34c3791e18df680a5cf312f6ff1260 ShipUp.AHKI (Trojan)
- ae4b716db77cd68cb0f1cb7971345ced ShellCode.CU (Trojan)
- aeab456e79e3674218acbf9b3d342187 ShellCode.CU (Trojan)
- a563ce41a7fd372b01ec4fb4bb8d3db0 ShipUp.AHKI (Trojan)
- 3ca0aa45ce02c21470800ececd433f31 ShipUp.AHKI (Trojan)
- bb27eb314630990d51206522ee3fd2bc Agent.FL (Trojan)
- 4da5ff526990b5126482dcd151f7789d Agent.FL (Trojan)
- d395fac36926af0bb84ce86a2899c60a Agent.FL (Trojan)
- 546a3025af00a70bdf7b89f5ad97b0e4 Agent.FL (Trojan)
- 93b56ff3345605f1dd08bf0175a72abd ASPM.GEN (Trojan)
- 4486f26e601d4983fe5b60a088e6053f Agent.FL (Trojan)
- 16a71ac5bd752d1aa8355f7160633fca BackDoor.AAM (Trojan)
- 72fedc43471d9aa1bc13b1d6890e25dd Agent.FL (Trojan)
- a93e789306d284dbe70e5f3db19a80a3 Dropper.GEN (Trojan)
- 1d1be478050ca2f9be47c5ecf0e8ad84 MalAgent.G (Trojan)
- c7f34ef7a2b9b2c4a1dfa7ea824bca93 Upx-48 (Trojan)
- 3e4f4fd7e20b67c422c6d40ea17df2b7 Ramnit
- bb3b32504829fe1c5324a9547270be16 Kovter.B (Trojan)
- d6e2ee16ee75bf4a3c8da8e9e3715b3d Upx-48 (Trojan)
- e5c02b1fe5fb3f1c37f4a416e482870a Agent.FL (Trojan)
- 71d776ccd4ab54ef45653da12e0c66c8 ShellCode.CU (Trojan)
- 28138c67f492e56414bff82a39b0781d agentTesla
- 8332b98416c224335d9d24d98fb35395 PA!MTB (Trojan)
Share This Article

An Article By
An Article By
Security News
Security News