Sonicwall RTDMI engine discovers malicious MS Office file containing Java RAT in the wild

Sonicwall RTDMI engine as part of Sonicwall Capture ATP service identified a new malicious Microsoft Office Document file embedded with a Java malware RAT (Remote Access Trojan) in real time. Among many of its previously announced detection capabilities, SonicWall RTDMI engine can also look inside multiple layers of packaging and obfuscation to find well entrenched malware components in real-time and provide unparalleled detection capabilities. The non-existence of this malicious file on popular malware search portals (VirusTotal or Reversing Labs) indicates how fresh the malware sample is in the wild and the effectiveness of RTDMI. The figure below was taken when we started analysis of this threat and found no results on Virustotal:

On opening the office document, it advises the victim to open the embedded olepackage to view the fake invoice. This fake invoice is actually a malicious Jar (Java-Archive) file:
Upon further analysis, Sonicwall Capture Labs threat researchers determined that the malicious jar file belongs to a notorious Java JRat family called Adwind. If the system has Java runtime installed, then upon opening this Jar file, it's malicious behaviour is exhibited. On execution, it drops a copy of itself into %temp% folder, drops a vbscript file and further downloads password recovery and other spying tools from internet into %temp% folder and executes them. It then proceeds to modify windows system registry to disable different antivirus and security software which are installed. It also disables System Restore from registry.
Few of the registry modifications are mentioned below:
- HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\SystemRestore
- "DisableConfig"=dword:00000001
- "DisableSR"=dword:00000001
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mbam.exe
- "debugger"="svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\FProtTray.exe
- "debugger"="svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\FortiClient.exe
- "debugger"="svchost.exe"
Indicators of Compromise:
- e8a3e9178d871b89db608615f663f7b09d6bad78421c3e1ce95c6776ed4df239 : Malicious Document File
- f1d0a8c11e4eed1165e9434c1dff914cf9c7baf5be1f528d026ee0f683f1ce26 : Malicious Java JRat File
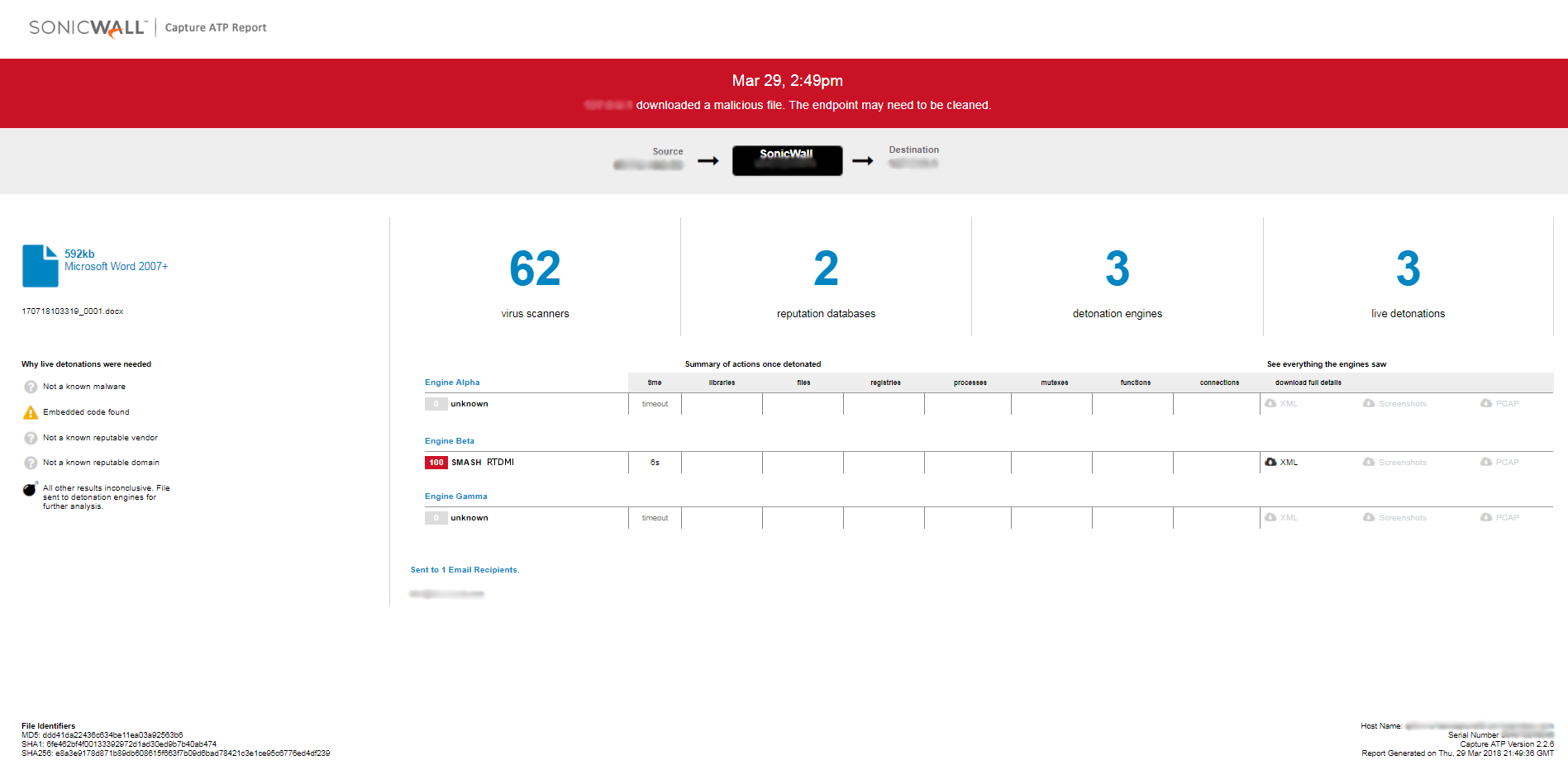
Evidence of the detection by RTDMI engine can be seen below in the Capture ATP report for this file:
Share This Article

An Article By
An Article By
Security News
Security News