Rethinking Security Architecture
Building Resilient Security Architectures with Adversary Behavior Frameworks
Introduction: The Complexity Problem
Today, enterprise businesses are regularly deploying new security technologies and services to address cybersecurity risks and threats. However, there are now too many vendors to manage. Overlapping features and complex integrations make the challenge even greater.
An article published by CSO Online outlines some of the top challenges of security tool integration:
- Too many security tools
- Lack of interoperability among tools
- Broken functionality
- Limited network visibility
- Increase in false alarms
- Failure to set expectations properly
- Lack of skills
At the same time, the distributed workforce and work-from-anywhere model demand secure, seamless access to resources across hybrid environments. Add cloud adoption into the mix, and things become even more complicated. The traditional on-premises security mindset simply isn’t enough to build secure architecture today — it’s no longer sufficient.
Why Do Security Professionals Struggle?
In cybersecurity, defenders rarely get the chance to know their adversaries. Attackers are intelligent, faceless and come from all walks of life. Security professionals must defend everything, while attackers need to find only one weakness to succeed.
According to the SonicWall 2025 Cyber Threat Report, 61% of the time, hackers leverage new exploit code within 48 hours.
As most security professionals will tell you, it’s not a matter of if an attack happens, but when. That’s why more organizations are shifting resources toward detecting and responding to threats as quickly as possible.
Using Cybersecurity Frameworks to Build Better Security Architecture
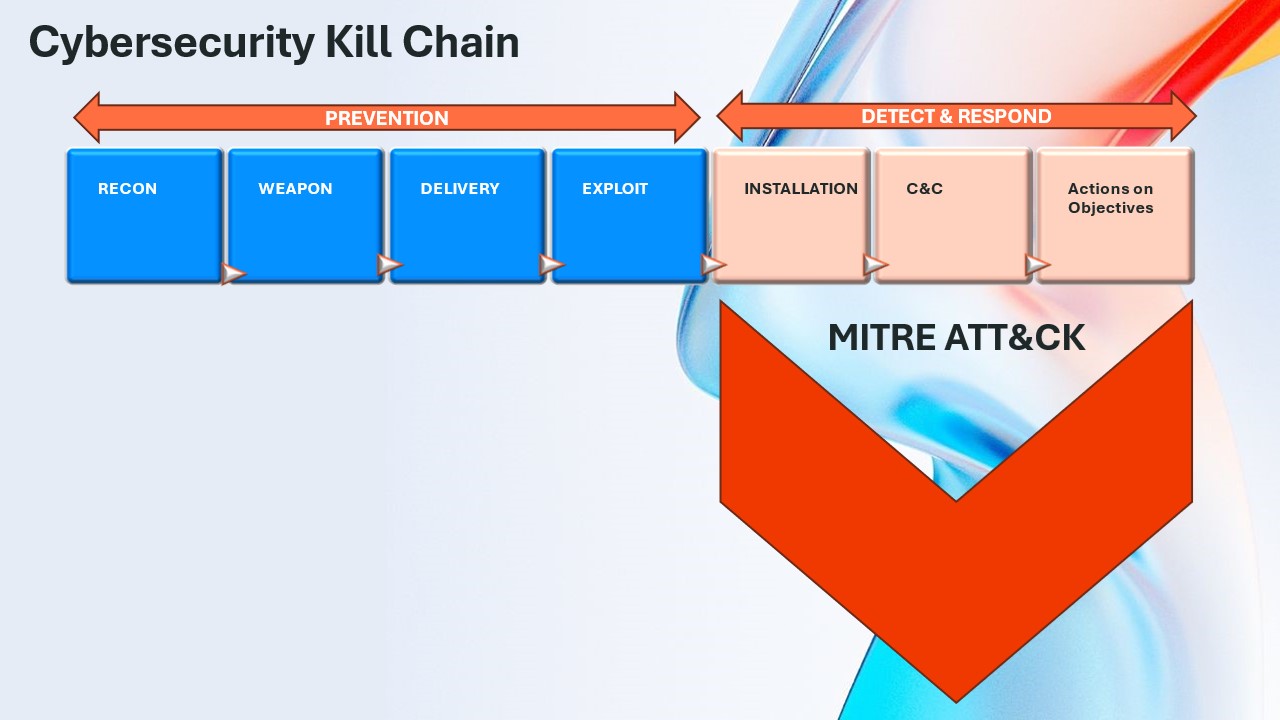
The Cybersecurity Kill Chain and MITRE ATT&CK® frameworks are excellent tools that offer insight into attacker behavior. They help security teams understand how technologies overlap to provide prevention and detection in a layered security architecture.
The Cybersecurity Kill Chain
Developed by Lockheed Martin, the Cybersecurity Kill Chain is a model describing the steps an attacker must complete to carry out a successful attack. The model consists of seven sequential stages:
- Reconnaissance
- Weaponization
- Delivery
- Exploitation
- Installation
- Command and control
- Actions on objectives
To stop an attack, one or more of these stages must be disrupted. If any link in the chain fails, the entire attack fails. Understanding these seven steps forms the foundation of an effective cybersecurity design.
MITRE ATT&CK®: Knowing the Adversary
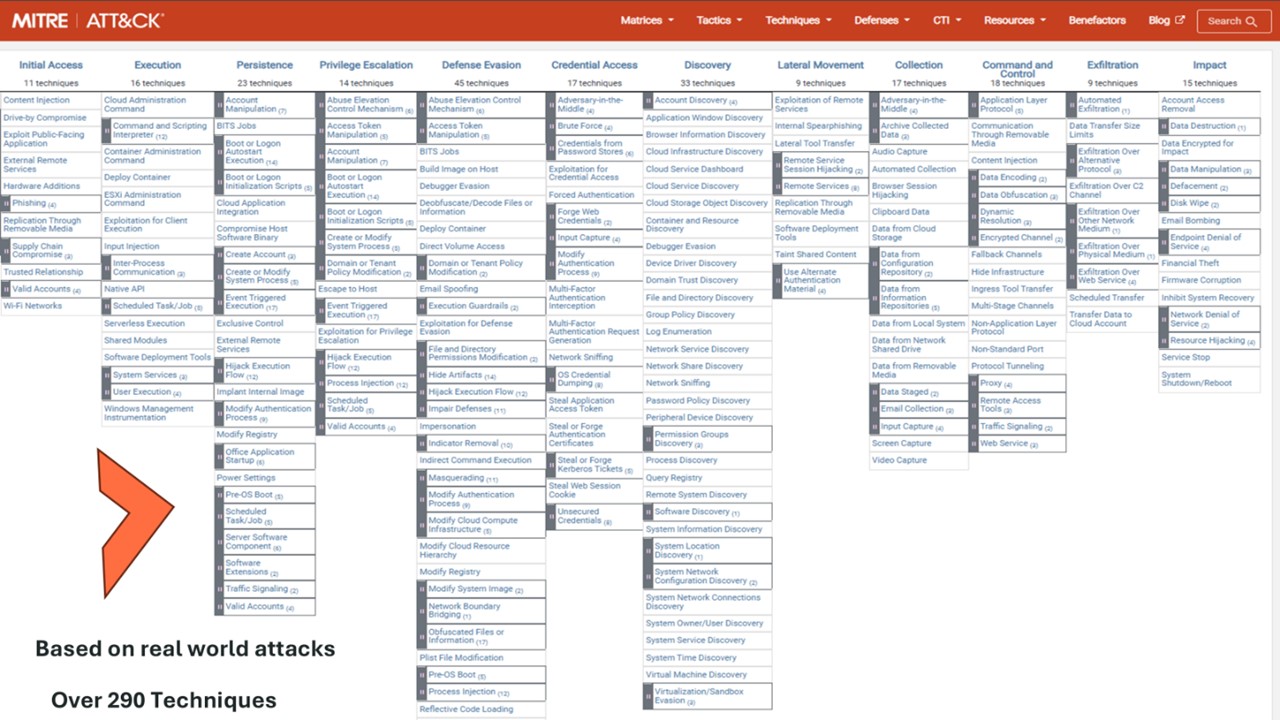
To build stronger detection and response layers, many organizations turn to the MITRE ATT&CK framework. It provides a comprehensive public database of attacker tactics, techniques, and procedures (TTPs). By studying this data, security professionals can better anticipate attacker behavior and tailor defenses accordingly.
Our earlier blogs on MITRE ATT&CK (Part 1 and Part 2) explore these ideas in greater detail, helping teams improve communication, accelerate response, and take a more proactive stance against threats.
The MITRE ATT&CK framework breaks down the final stages of the kill chain — installation, command and control, and actions on objectives — into 12 granular categories based on real-world research from millions of attacks. The ATT&CK matrix lists more than 290 adversary techniques.
For cybersecurity teams, this is a gold mine of information to identify security gaps and test network resilience. Up to this point, prevention has been the focus — stopping attacks before they begin. But once an attacker is inside, detection and response become critical.
The Role of XDR and SASE in Modern Security Architecture
Disruptive technologies such as Extended Detection and Response (XDR) and Secure Access Service Edge (SASE) help organizations simplify and consolidate their architectures. They remove overlapping tools in the prevention layer and strengthen the detection and response layer.
When planning vendor consolidation, the goal shouldn’t be cost savings alone. Instead, the focus should be on streamlining architecture to reduce integration friction and improve security outcomes.
How SonicWall Helps Solve This Challenge
SonicWall has transformed significantly in recent years. Today, it delivers end-to-end cybersecurity — from endpoint to cloud — backed by advanced threat research and both fully managed and co-managed services. All of this is unified under a single management console that provides partners with full visibility, simplified alert handling, and streamlined account management.
.JPG)
Security platform vendors like SonicWall, with Managed XDR and Secure Service Edge (SSE) solutions such as Cloud Secure Edge (CSE), help businesses consolidate vendors, reduce complexity, and improve risk posture in the preventive layer. At the detection and response layer, SonicSentry MXDR delivers 24/7 SOC monitoring and incident response to protect customers across the attack surface.
.JPG)
Benefits of SonicWall MXDR
- Rapid threat mitigation: 24/7 SOC monitoring and response to stop attacks in real time, minimize damage, and protect customers in an evolving landscape.
- Unified SOC across the attack surface: Correlates data across endpoint, cloud, and identity for stronger detection and better visibility.
- Reduced alert fatigue: Filters and escalates only critical alerts, ensuring no key threat goes unnoticed.
- Flexible billing: No contracts or long-term commitments — scale services monthly based on business needs.
- No minimums: Suitable for organizations of all sizes, from small businesses to large enterprises.
- White-glove onboarding: Expert-led proof-of-concept and setup assistance.
- Cyber warranty: When combined with SonicWall firewalls, includes additional financial protection through an embedded cyber warranty.
Conclusion
.JPG)
The cybersecurity landscape has become too complex for fragmented tools and siloed management. By combining the Cybersecurity Kill Chain and MITRE ATT&CK frameworks and mapping them to prevention, detection, and response layers, organizations can pursue vendor consolidation and build architectures that are more resilient and future-ready.
We hope you found this useful. To learn more, visit our resource center or our page on SonicSentry MXDR.
Questions or comments? Contact Rajesh Agnihotri at ragnihotri@sonicwall.com.
Share This Article

An Article By
An Article By
Rajesh Agnihotri
Rajesh Agnihotri

