P2P Worm Spreading in the Wild (Nov 24, 2010)

SonicWALL UTM Research team received reports of a new variant of a Peer-to-Peer (P2P) Worm spreading in the wild. It propagates through P2P channels as well as spammed e-mail. The e-mail contains the malicious file inside the zip attachment.
Below are sample e-mails:
Subject:
- You have got a new message on Facebook!
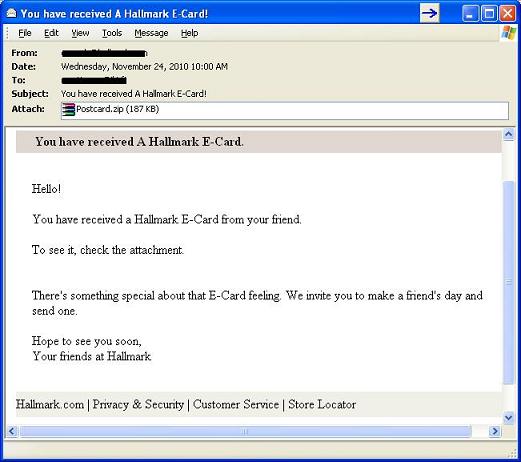
- You have received A Hallmark E-Card!
Attachment:
- Facebook message.zip (contains document.htm .exe )
- Postcard.zip (contains document.htm .exe )
Email Body:
- Hi,
You have got a personal message on Facebook from your friend.
To read it please check the attachment.
Thanks,
The Facebook Team
===================================================
Hello!
You have received a Hallmark E-Card from your friend.
To see it, check the attachment.
There's something special about that E-Card feeling. We invite you to make a friend's day and send one.
Hope to see you soon,
Your friends at Hallmark
===================================================
The e-mail message looks like below:

===================================================
Once the user runs the executable file, it will do the following activities:
File Operation:
Added Files
- Documents and Settings{user}Application DataSystemProclsass.exe - (172KB) [ Detected as GAV: Injector.CQX (Worm) ]
- WINDOWSsystem32HPWuSchdi.exe - (320KB) [ Detected as GAV: Injector.CQX (Worm) ]
- Program FilesMozilla Firefoxextensions{9CE11043-9A15-4207-A565-0C94C42D590D}
- Program FilesMozilla Firefoxextensions{9CE11043-9A15-4207-A565-0C94C42D590D}chrome
- Program FilesMozilla Firefoxextensions{9CE11043-9A15-4207-A565-0C94C42D590D}chromecontent
- Program FilesMozilla Firefoxextensions{9CE11043-9A15-4207-A565-0C94C42D590D}chromecontenttimer.xul [ Detected as GAV: Dursg.G (Trojan) ]
- Program FilesMozilla Firefoxextensions{9CE11043-9A15-4207-A565-0C94C42D590D}chrome.manifest
- Program FilesMozilla Firefoxextensions{9CE11043-9A15-4207-A565-0C94C42D590D}install.rdf
Registry Operation:
Added Entries
- HKEY_CURRENT_USERIdentities Curr version "25"
- HKEY_CURRENT_USERIdentities Last Date "24-11-2010"
- HKEY_CURRENT_USERIdentities Inst Date "24-11-2010"
- HKEY_CURRENT_USERIdentities Popup count "0"
- HKEY_CURRENT_USERIdentities Popup time "0"
- HKEY_CURRENT_USERIdentities Popup date "0"
- HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionpoliciessystem EnableLUA dword:00000000
- KEY: HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun
Value: HP Software Updater v1.3
Data:"WINDOWSSystem32HPWuSchdi.exe" - KEY: HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionpoliciesExplorerRun
Value: RTHDBPL
Data:"Documents and Settings{user}Application DataSystemProclsass.exe" - KEY: HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesSharedAccessParametersFirewallPolicyStandardProfileAuthorizedApplicationsList
Value: C:WINDOWSSystem32HPWuSchdi.exe
Data:"C:WINDOWSSystem32HPWuSchdi.exe:*:Enabled:Explorer"
Allows program to run without user notification:
Ensures this Worm runs on every Windows startup.
Ensures this Worm bypass the Firewall.
Malware Propagation:
- Peer-to-Peer Applications
- program fileswinmxshared
- program filesteslafiles
- program fileslimewireshared
- program filesmorpheusmy shared folder
- program filesemuleincoming
- program filesedonkey2000incoming
- program filesbearshareshared
- program filesgrokstermy grokster
- program filesicqshared folder
- program fileskazaa lite k++my shared folder
- program fileskazaa litemy shared folder
- program fileskazaamy shared folder
- AOL Instant Messenger (AIM) Hacker.exe
- AOL Password Cracker.exe
- Ad-aware 2010.exe
- Adobe Acrobat Reader keygen.exe
- Adobe Illustrator CS4 crack.exe
- Adobe Photoshop CS4 crack by M0N5KI Hack Group.exe
- Alcohol 120 v1.9.x.exe
- Anti-Porn v13.x.x.x.exe
- AnyDVD HD v.6.3.1.8 Beta incl crack.exe
- Ashampoo Snap 3.xx .exe
- Avast 4.x Professional.exe
- Avast 5.x Professional.exe
- BitDefender AntiVirus 2010 Keygen.exe
- Blaze DVD Player Pro v6.52.exe
- Brutus FTP Cracker.exe
- CleanMyPC Registry Cleaner v6.02.exe
- Counter-Strike Serial key generator .exe
- DCOM Exploit archive.exe
- DVD Tools Nero 10.x.x.x.exe
- Daemon Tools Pro 4.8.exe
- DivX 5.x Pro KeyGen generator.exe
- Divx Pro 7.x version Keymaker.exe
- Download Accelerator Plus v9.2.exe
- Download Boost 2.0.exe
- FTP Cracker.exe
- G-Force Platinum v3.7.6.exe
- Google SketchUp 7.1 Pro.exe
- Grand Theft Auto IV .exe
- Half-Life 2 Downloader.exe
- Hotmail Cracker .exe
- Hotmail Hacker .exe
- ICQ Hacker Trial version .exe
- IP Nuker.exe
- Image Size Reducer Pro v1.0.1.exe
- Internet Download Manager V5.exe
- K-Lite Mega Codec v5.2 Portable.exe
- K-Lite Mega Codec v5.2.exe
- Kaspersky AntiVirus 2010 crack.exe
- Kaspersky Internet Security 2010 keygen.exe
- Keylogger unique builder.exe
- L0pht 4.0 Windows Password Cracker.exe
- LimeWire Pro v4.18.3 .exe
- MSN Password Cracker.exe
- Magic Video Converter 8.exe
- McAfee Total Protection 2010 .exe
- Microsoft Visual Basic KeyGen.exe
- Microsoft Visual C++ KeyGen.exe
- Microsoft Visual Studio KeyGen.exe
- Microsoft.Windows 7 ULTIMATE FINAL activator+keygen x86.exe
- Motorola, nokia, ericsson mobil phone tools.exe
- Mp3 Splitter and Joiner Pro v3.48.exe
- Myspace theme collection.exe
- NetBIOS Cracker.exe
- NetBIOS Hacker.exe
- Norton Anti-Virus 2005 Enterprise Crack.exe
- Norton Anti-Virus 2010 Enterprise Crack.exe
- Norton Internet Security 2010 crack.exe
- PDF password remover (works with all acrobat reader).exe
- Password Cracker.exe
- Power ISO v4.4 + keygen milon.exe
- Rapidshare Auto Downloader 3.8.6.exe
- Sophos antivirus updater bypass.exe
- Sub7 2.5.1 Private.exe
- Super Utilities Pro 2009 11.0.exe
- Total Commander7 license+keygen.exe
- Tuneup Ultilities 2010.exe
- Twitter FriendAdder 2.3.9.exe
- UT 2003 KeyGen.exe
- VmWare 7.x keygen.exe
- Website Hacker.exe
- WinRAR v3.x keygen .exe
- Winamp.Pro.v7.xx.PowerPack.Portable+installer.exe
- Windows 2008 Enterprise Server VMWare Virtual Machine.exe
- Windows Password Cracker + Elar3 key.exe
- Windows2008 keygen and activator.exe
- YouTubeGet 5.6.exe
- Youtube Music Downloader 1.3.exe
- [+ MrKey +] Windows XP PRO Corp SP3 valid-key generator.exe
- Vmvare keygen.exe
- Windows 7 Ultimate keygen.exe
- Troj
an Killer v2.9.4173.exe - RapidShare Killer AIO 2010.exe
- Nero 9.x keygen.exe
- Absolute Video Converter 6.2-7.exe
- PDF Unlocker v2.0.5.exe
- PDF to Word Converter 3.4.exe
- sdbot with NetBIOS Spread.exe
This Worm drops copies on P2P shared folders using filenames taken from its list:
List of the P2P apps:
Filenames it uses when copying itself to P2P folders which are key generator and cracking tools of popular commercial applications:
Mass-Mailing
This Worm harvests email addresses from the system and send spam emails with an attachment of itself.
Network Activity:
The following HTTP request were observed from this Worm:
- http://controll{REMOVED}ckout
Pop-up Advertisements
- This Worm injects code to the following browser to monitor keyword searches:
- Internet Explorer
- Opera
- Chrome
- Firefox
- google</>
- search</>
- yahoo</>
- live</>
- msn</>
- bing</>
- youtube</>
- airlines
- amazon
- antivir
- antivirus
- baby
- bank
- bany
- baseball
- books
- cars
- casino
- cialis
- cigarettes
- comcast
- craigslist
- credit
- dating
- design
- diet
- doctor
- dvd
- ebay
- estate
- fashion
- film
- finance
- flights
- flower
- footbal
- football
- gambling
- game
- gifts
- golf
- graphic
- health
- hotel
- insurance
- iphone
- ipod
- job
- loan
- loans
- medical
- military
- mobile
- money
- mortgage
- movie
- music
- myspace
- pharma
- pocker
- poker
- porn
- school
- sex
- shop
- software
- sport
- spybot
- spyware
- trading
- tramadol
- travel
- verizon
- video
- virus
- vocations
- wallpaper
- weather
- yobt
The following are the search domains this worm monitors for keyword terms:
The following are the keyword terms it monitors and once found displays pop-up advertisements from the domain "tetrosearch.com" or "oxoblaster.com":
The Worm is also known as Worm/BlackControl.H , Inject-AAI and Troj/Agent-OLK
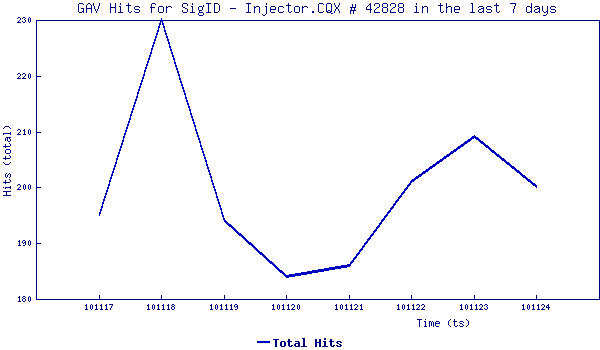
SonicWALL Gateway AntiVirus provides protection against these Worm via the following signatures:
- GAV: Injector.CQX (Worm)
- GAV: Dursg.G (Trojan)
Share This Article

An Article By
An Article By
Security News
Security News