Oracle Identity Manager Authentication Bypass Vulnerability (CVE-2025-61757)

Overview
The SonicWall Capture Labs threat research team became aware of an authentication bypass flaw in Oracle Identity Manager, assessed their impact, and developed mitigation measures. Oracle Identity Manager (OIM) is an identity management solution that automates the user lifecycle, from provisioning to de-provisioning, across various applications and resources, both on-premises and in the cloud.
The unauthenticated authentication bypass vulnerability, identified as CVE-2025-61757, has been discovered in Oracle Identity Manager's REST Web Services component, affecting versions 12.2.1.4.0 and 14.1.2.1.0. These flaws enable remote, unauthenticated attackers to manipulate request paths and bypass URI filtering logic. Successful exploitation enables attackers to invoke sensitive functions without authentication, potentially leading to full compromise of identity management workflows, privilege escalation, and unauthorized account operations. Flagged by CISA, CVE-2025-61757 enables an adversary to circumvent authentication/ login controls, allowing them to achieve pre-authentication RCE. Hence, all organizations that use Oracle Identity Manager (OIM) are strongly encouraged to update their instances to the latest patched version as a matter of urgency.
Technical Overview
At the heart of the vulnerability lies the core issue: REST Web Services component. The vulnerability stems from an authentication bypass in Oracle Identity Manager’s REST APIs, where attackers can trick the SecurityFilter into treating protected endpoints as public by appending parameters such as? WSDL or. wadl to the URL path.
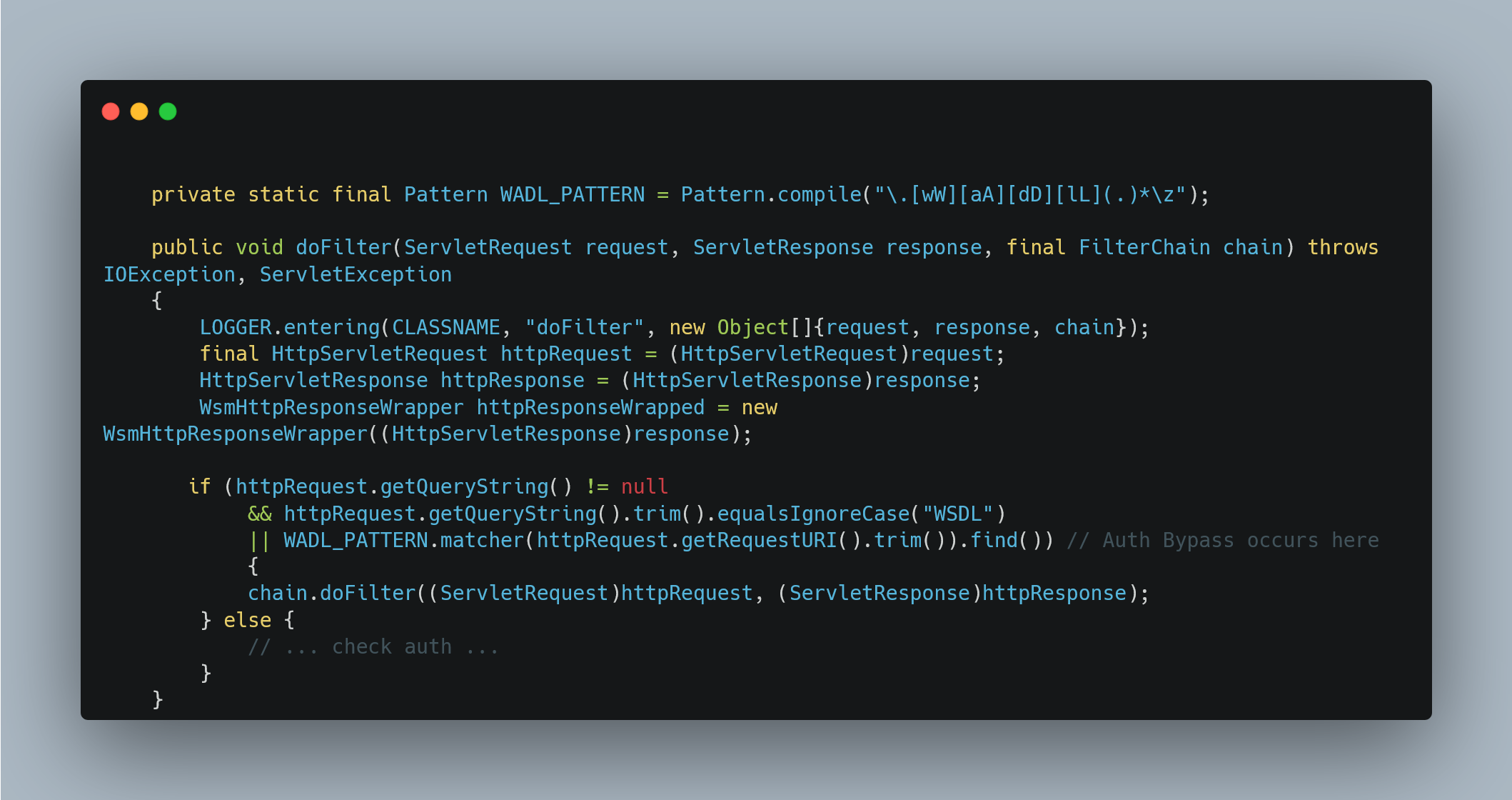
All URLs that end in “. wadl” are exempt from authentication. Adding just “. wadl” to a URL would not work, as this would point to a different, non-existent file; however, attackers can use Java’s path parameter and craft a URL ending with “;.wadl” as seen in Figure 2. After gaining unauthenticated access, attackers can interact with a Groovy script compilation endpoint. Although this endpoint is not intended to execute scripts, it can be exploited to run malicious code during the compilation process by abusing Groovy’s annotation-processing feature. This flaw chain allowed researchers to achieve pre-authentication remote code execution on vulnerable Oracle Identity Manager instances.
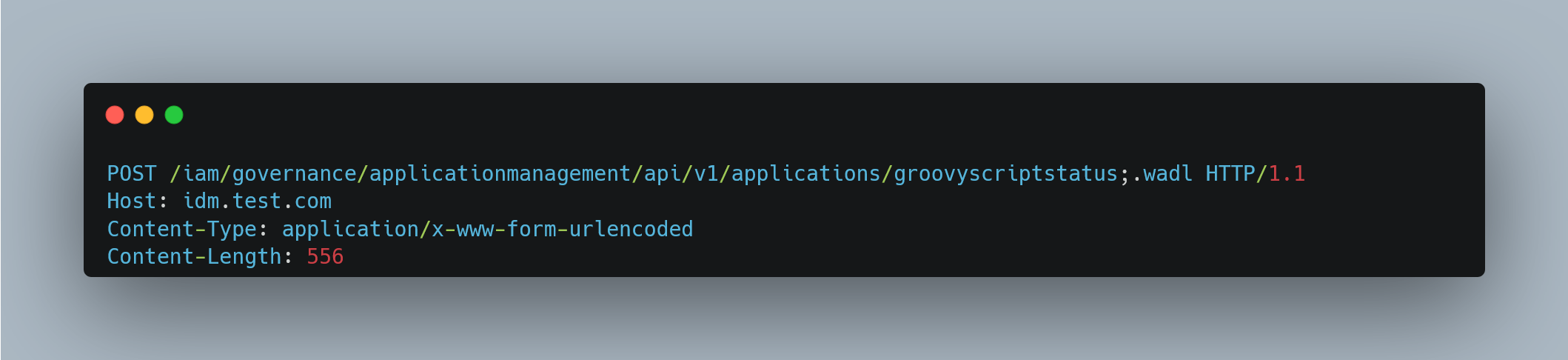
Exploitation
Successful exploitation of CVE-2025-12480 allows remote, unauthenticated attackers to achieve Remote Code Execution (RCE) in vulnerable Oracle Identity Manager. This vulnerability is easily exploitable, requires no privileges or user interaction, and can impact all aspects of security - confidentiality, integrity, and availability. The vulnerability is classified under CWE-306 (Missing Authentication for Critical Function).
With a public PoC available on Github, exploitation is feasible with ease, provided vulnerable instances are still not patched.
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:
- IPS:21711 - Oracle Fusion Middleware Authentication Bypass
Remediation Recommendations
Given that adversary can circumvent authentication allowing them to achieve RCE and potentially pivot into wider Oracle Cloud infrastructure users are strongly advised to upgrade their instances to the latest patched version as outlined in the official vendor advisory. Additionally, use the signature mentioned above and confirm that every Oracle Identity Manager instance in the environment is updated to a patched release and verify that “. wadl” resources are not directly reachable from untrusted networks.
Relevant Links
Share This Article

An Article By
An Article By
Dhiren Vaghela
Dhiren Vaghela
Dhiren Vaghela has over a decade of experience in the IPS domain, with a strong focus on defensive security. His expertise lies in identifying, analyzing and mitigating vulnerabilities. Dhiren is well-versed in content-based signature writing, scanner-based alert generation and technical blog writing. By leveraging emerging technologies, he has developed numerous IPS signatures across various protocols. Known for his exceptional signature writing skills and collaborative team spirit, Dhiren is a valuable asset in the field of cybersecurity.
