New variant of Adwind RAT is active in the wild

SonicWall Capture Labs Threat Research team spotted a new variant of adwind RAT, a cross-platform, multi-functional malware also known as JRAT that silently steals system information and credentials from the infected machines.
This phishing campaign targets commercial industries with a message crafted to look like a legitimate vendor and with an attachment "Remittance advice.pdf". But there is no real attachment, just a clickable image embedded at the top of the mail, made to look like a PDF file attachment. When user clicks on the image, it takes the user to the malicious website that drops the initial payload, "Remittance_Advice_HEAD0000I00231_pdf.jar". The payload is a malicious Java archive (.JAR) file but attacker has made it look like a PDF by hiding it's true extension.
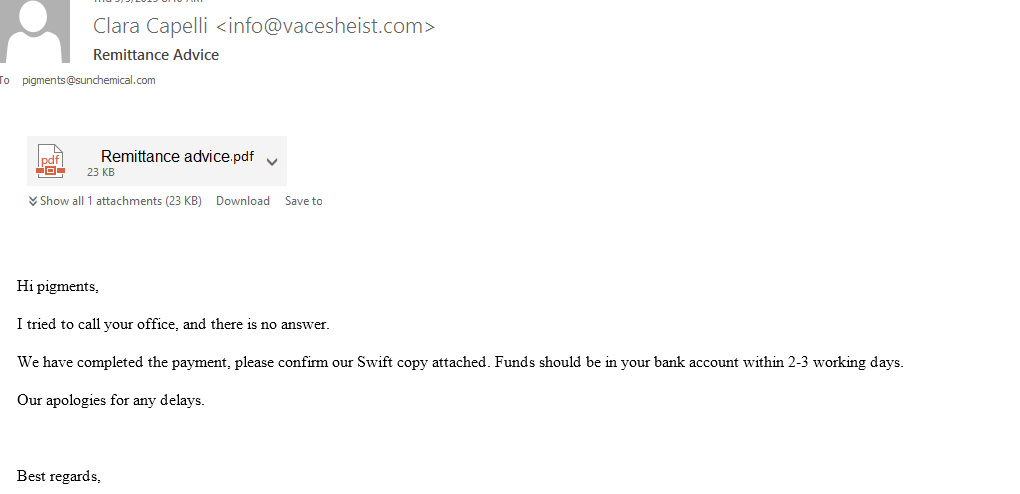
It's just an image with an embedded hyperlink not an actual attachment
Based on the information from the Urlscan.io, this malicious jar payload is available on the below websites since September 25th.
Once executed, it connects with the Command & Control Server, downloads more payloads, installs dependencies and starts harvesting system information and user credential.
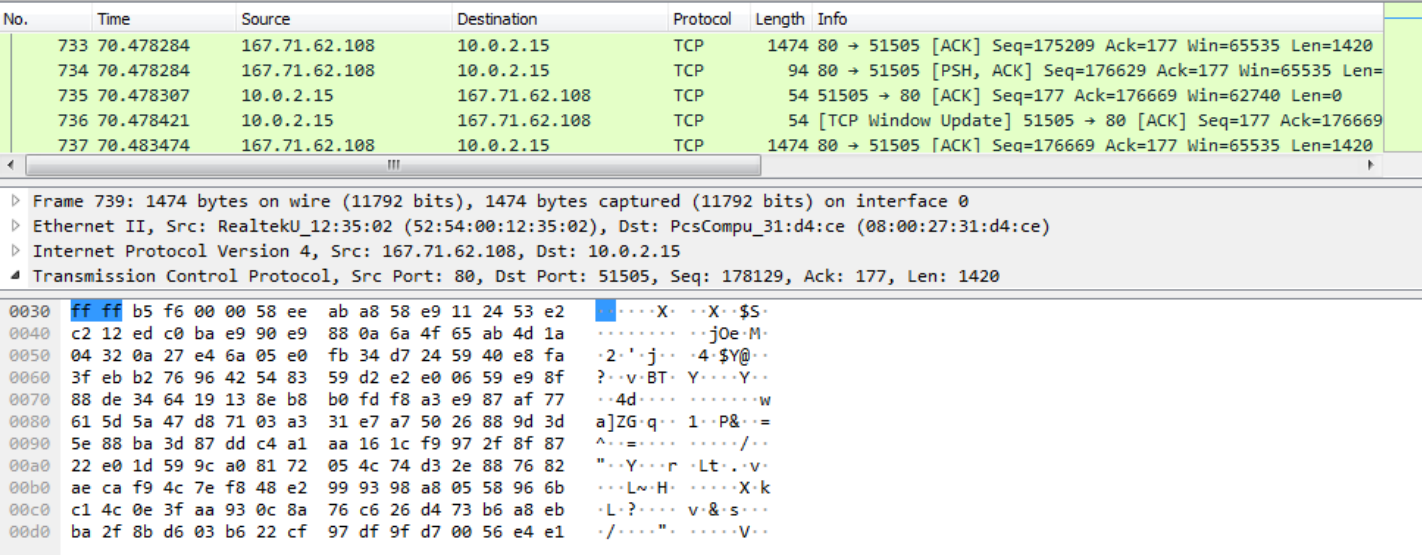
It tries to find the external IP address of the infected machine through "http://bot.whatismyipaddress.com"
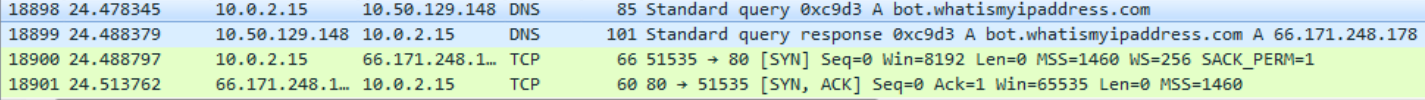
JAR file executes the below shell command to change the default code page format to 1252 by calling CHCP (Change Code Page utility) and later executes the PowerShell command.

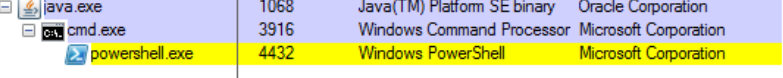
It drops the below executables into the temp directory:
- sqlite-3.8.11.2-f1c6f213-9b29-4f05-8db4-69507f2eee1b-sqlitejdbc.dll
- jna990208984750515170.dll
It starts stealing user credential and configuration information by querying various applications path.
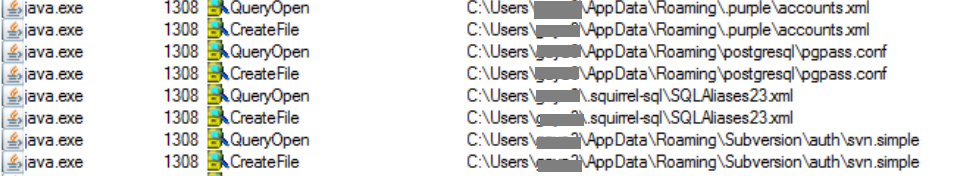
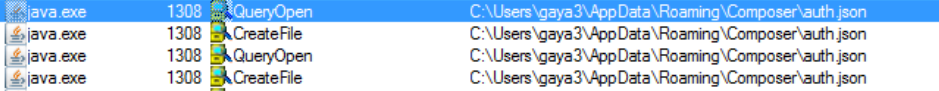
This variant must be from the same attacker group that targeted National grid utilities last month as there are similarities in the email message and the payload format. In the previous campaign, JAR file executes VB script but this campaign uses PowerShell script.
It seems very active in the last few days but not many security vendors detect this at the time of writing this article.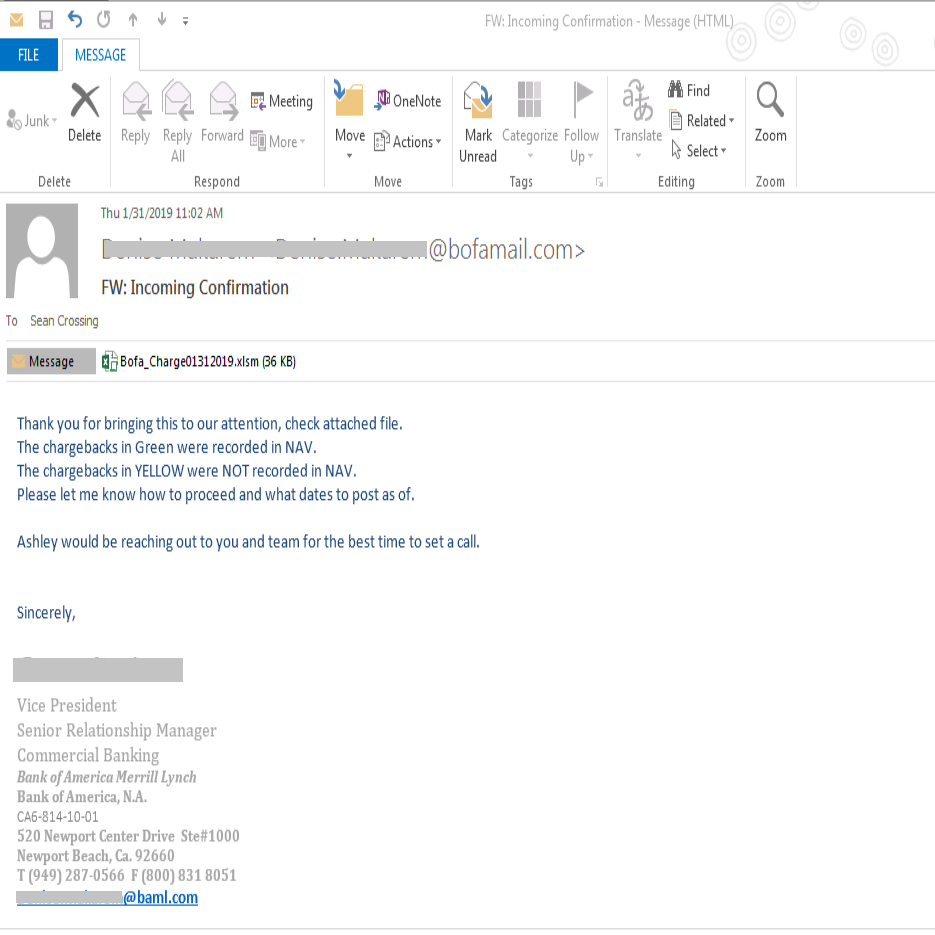
The Java archive has 212 class files and they are heavily obfuscated. It is then decompiled using Procyon decompiler, 177 class files are found to be obfuscated and the remaining files are encrypted using the AES encryption algorithm. We manually deobfuscated the code to retrieve the encryption details.
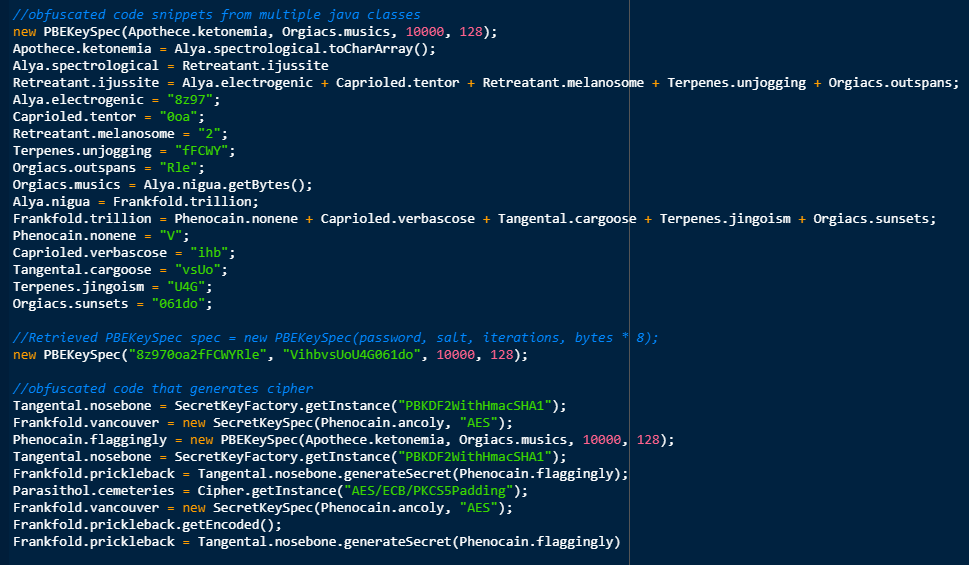
It uses the AES-128 symmetric encryption algorithm. We retrieved the code below that creates the cipher object with the AES key. This object shall be used to decrypt the encrypted JAR file contents.

VirusTotal Threat Graph:
SonicWALL Capture Labs Threat Research team provides protection against this threat with the following signatures:
- GAV 1383 Adwind.J1
- GAV 9359 Adwind.KM_3
- GAV 9358 Adwind.KM_2
- GAV 28381 Adwind.FMAE_12
- GAV 29093 Adwind.FMAE_11
- GAV 28975 Adwind.FMAE_10
- GAV 29046 Adwind.A_4
- GAV 21749 Adwind.FMAE_5
- GAV 35919 Adwind.AG
- GAV 23867 Adwind.H_11
- GAV 19558 Adwind.Z_24
- GAV 19490 Adwind.Z_11
- GAV 33012 Adwind.V_3
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.
- 6e8cf485eacacfc00e3dcb5049c6c49230f8f845949ef24794eb457e0a27b7fc
- 25ab334bfbc9c5ffc7e2223338c25a50124386b600582074ec65148c74ee4e32
- 5d0829452303936130c6cd126aa11460c334908c6220e3f833e6d301e51df1e3
- 28ef8087d1ed5e15a072029e6a910f42f41c8953a75d064182801d63d04dad06
- 3877128c64e2c4f66f6f3ef6f6b1a46054a2c7ee56ec73a67230fabdeb75808e
- c2b94a3cdaa2f32919d7a8486403a53ef73f521723b2ba69764a961b2e63cfe5
- kalemimintelvesi.com
- osixresort.com
- midc-ict.com
- fatacosmetics.com
- tricascadetech.co.uk
IP:
167.71.62.108:80
Share This Article

An Article By
An Article By
Security News
Security News