More Adobe Flash (SWF) Exploits Discovered in the Wild for CVE-2015-5119

More Adobe Flash (SWF) Exploits Discovered in the Wild for CVE-2015-5119
CVE-2015-5119 is a Use-after-free vulnerability in the ByteArray class in the ActionScript 3. Adobe first released the advisory for CVE-2015-5119 in July and the first exploit surfaced soon. We continue to observe new exploits in the wild.
A typical type of exploit using this vulnerability is to add an extra layer of obfuscation to the exploit Action Script code into a second flash file--which is embedded as a binary within the outer Flash file. The following image shows the decompiled outer SWF file. Here you can see that there is a binary byte array included in in the outer SWF file:
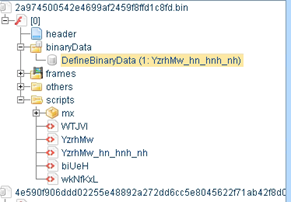
This image shows the encrypted bytes of the binary file (which will be retrieved through a ByteArrayAsset class of Action Script and decoded):
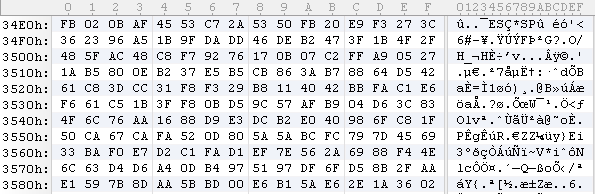
The following function decodes the binary with an embedded key and obfuscated system function calls:
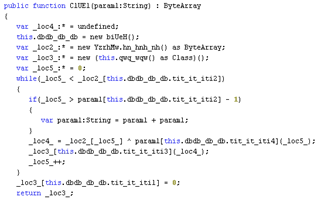
This image shows the binary of the embedded Flash file after decryption:
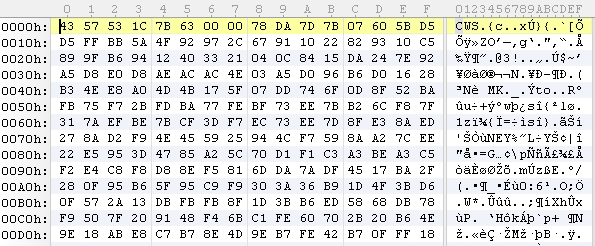
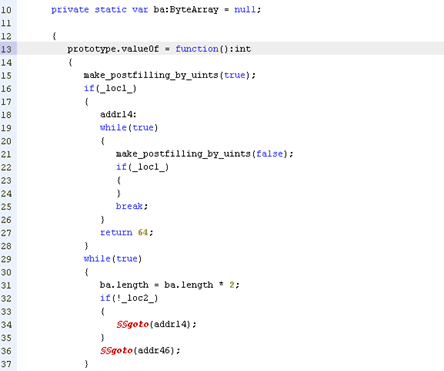
Finally, we can see the exploit code for CVE-2015-5119 that resides inside the inner SWF file. This exploit uses the valueOf property on a ByteArray:
Dell SonicWALL has observed hundreds of the exploits using the flash wrapping method in the wild since July. Multiple GAV signatures have been created to protect the customers. The following are some of them:
- 28005 CVE-2015-5119.AJ
- 27997 CVE-2015-5119.C_3
- 27992 CVE-2015-5119.A_17
- 19262 CVE-2015-5119_3
- 18484 CVE-2015-5119_2
- 18363 CVE-2015-5119.AN_2
- 16398 CVE-2015-5119.C_4
- 16399 CVE-2015-5119.C_5
Share This Article

An Article By
An Article By
Security News
Security News