LB-LINK Router Command Injection Vulnerability

LB-Link is a well-known company in the networking industry that specializes in the design, manufacturing, and distribution of wireless networking products. The company's product portfolio includes a wide range of wireless routers, network adapters, Wi-Fi extenders, and other networking accessories.
A command injection vulnerability exists in LB-LINK's BL-AC1900, BL-WR9000, BL-X26 and BL-LTE300 wireless routers.
Command Injection Vulnerability
The goal of a command injection attack is the execution of arbitrary commands on the host operating system via a vulnerable application. Command injection attacks are possible when an application passes unsafe user-supplied data (forms, cookies, HTTP headers etc.)
LB-LINK Routers Command Injection | CVE-2023-26801
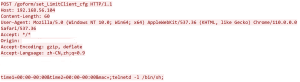
As seen from the exploit, the command injection vulnerability is possible due to the insufficient input validation of the 'mac' parameter. In the payload the value  is appended to the 'mac' parameter . This value is a command injection attempt. This parameter value attempts to execute the 'telnetd' command with the 'l' option to start a new login shell (/bin/sh). This is how an unauthorized attacker can send crafted requests to /goform/set_LimitClient_cfg, and execute arbitrary commands on remote devices.
is appended to the 'mac' parameter . This value is a command injection attempt. This parameter value attempts to execute the 'telnetd' command with the 'l' option to start a new login shell (/bin/sh). This is how an unauthorized attacker can send crafted requests to /goform/set_LimitClient_cfg, and execute arbitrary commands on remote devices.
Following LB-LINK's router versions are vulnerable :
- BL-AC1900_2.0 V1.0.1
- BL-WR9000 V2.4.9
- BL-X26 V1.2.5
- BL-LTE300 V1.0.8
The CVSS (Common Vulnerability Scoring System) score is 9.8 with CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
- Attack vector is network.
- Attack complexity is low.
- Privileges required is none.
- User interaction is none.
- Scope is unchanged.
- Impact of this vulnerability on data confidentiality is high.
- Impact of this vulnerability on data integrity is high.
- Impact of this vulnerability on data availability is high.
SonicWall Capture Labs provides protection against this threat via following signature:
- IPS 15851:LB-LINK Routers Command Injection
Threat Graph
Share This Article

An Article By
An Article By
Security News
Security News