Found another Remote Access Trojan pretending to be Documentation on Covid19 Response and Preparedness

As the Corona virus pandemic unfolds, the Sonicwall Capture labs Research team also observe an increasing amount of malicious software actively exploiting this crisis. As we have previously reported, we have seen different malware families using this tactic from ransomware, to infostealers, to phishing scam trying to scheme people who are in constant search for news and updates from around the world.
This week, we have seen a malware family pretending to be information regarding the virus and targeting administrators of institutions for higher education.
Infection Cycle
The Trojan arrives in an archive possibly distributed via spam. Within that archive is a file with the following filename and icon:
- Interim Guidance for Administrators of US Institutions of Higher Education to Plan, Prepare and Respond to CoViD19.exe
![]()
In fact the official statement from CDC (Centers for Disease Control and Prevention) concerning the above can be found on this official webpage which has the same title.
Upon execution it creates a copy of itself in the following directory:
- %Appdata%\Roaming\shost.exe
To ensure persistence it adds the following to the registry:
- HKCU/Software\Microsoft\Windows\CurrentVersion\Run shost %Appdata%\Roaming\shost.exe
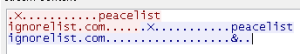
It then makes a DNS query to peacelist ignorelistcom:
And then makes periodic connections to a remote server using ports 5505, 7707, 8808.
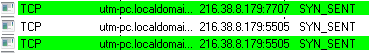
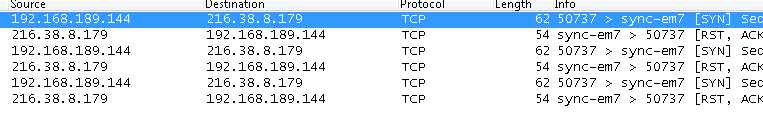
At the time of analysis, no data has been exchanged, received nor sent. But certainly this demonstrated its ability to phone home and possibly receive further instructions from the remote server.
During this crisis, we urge our users to only use official and reputable websites as their source of information and news. Always be vigilant and cautious when installing software programs particularly if you are not certain of the source.
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: Async.RAT (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions
Share This Article

An Article By
An Article By
Security News
Security News