Buffalo routers path traversal vulnerability

SonicWall Capture Labs threat research team observed attacks exploiting vulnerability in Buffalo routers.
Buffalo company builds quality storage, networking, and other technology-related solutions. Their network attached storage (NAS) devices, many with scale-as-you-go options, are installed with pre-tested hard drives that eliminate the hassle of sourcing and testing drives, saving you time and money. Buffalo also builds Wireless Router which is a high speed, open source dual band solution, and is ideal for creating a high speed 11ac wireless home network. A path traversal vulnerability exists in web interface of certain firmware versions of these routers.
Vulnerability | CVE-2021-20090
A path traversal attack (also known as directory traversal) aims to access files and directories that are stored outside the web root folder by manipulating variables that reference files with dot-dot-slash sequences. A path traversal vulnerability in the web interfaces of Buffalo WSR-2533DHPL2 firmware version <= 1.02 and WSR-2533DHP3 firmware version <= 1.24 could allow unauthenticated remote attackers to bypass authentication. Successful exploitation of this vulnerability could allow an attacker to access pages that would otherwise require authentication. An unauthenticated attacker could gain access to sensitive information, including valid request tokens, which could be used to make requests to alter router settings.
The vulnerability exists due to a list of folders which fall under a "bypass list" for authentication. One such folder is images . The exploit looks like this
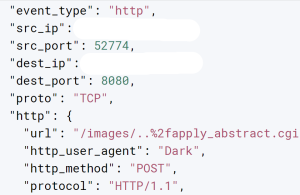

The attacker is able to bypass authentication through path traversal. The attacker uses POST request to access and modify the configuration of the attacked device. The attacker then downloads and executes malicious script from attacker controlled server .
Following versions are vulnerable:
- WSR-2533DHPL2 firmware version <= 1.02
- WSR-2533DHP3 firmware version <= 1.24
The Vendor advisory is here.
SonicWall Capture Labs provides protection against this threat via following signatures:
-
-
- IPS 15659:Buffalo Routers Configuration File Injection
- GAV: Shell.LOL
-
Threat Graph
IoCs
212.192.241.87
054320be2622f7d62eb6d1b19ba119d0a81cb9336018d49d9f0647706442ae8f
Share This Article

An Article By
An Article By
Security News
Security News