Android Ransomware spreading as codec pack installer

SonicWALL Threats Research Team received reports of yet another ransomware for Android which encrypts the files on a device and demands a ransom in exchange of potentially unlocking the content.
Infection Cycle
The malware requests for the following permissions during installation:
- internet
- get tasks
- kill background processes
- access fine location
- receive sms
- access coarse location
- call phone
- vibrate
- read sms
- write sms
- send sms
- read contacts
- read phone state
- system alert window
- wake lock
- disable keyguard
- receive boot completed
- write external storage
- read external storage
- quickboot poweron
Upon execution it sends a GET request to the domain fsdf2tvwev-ru.1gb.ru. This is a general behavior exhibited by malware where they register/inform the attacker about the infection on a device. The name of the webpage (reg.php) is another indication of this behavior. Unfortunately we get a base 64 encoded response that states as error:
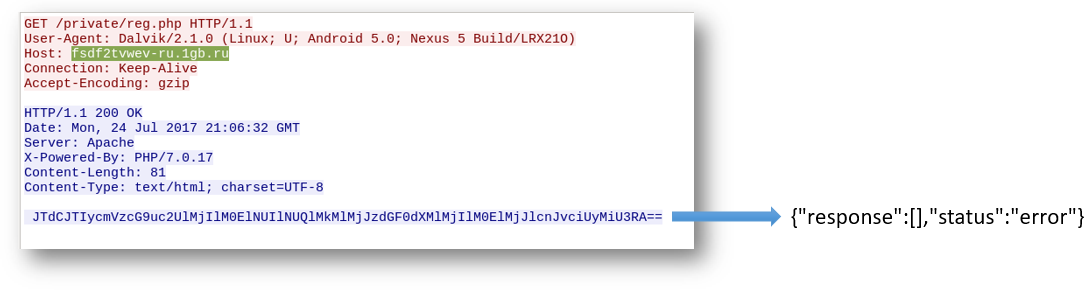
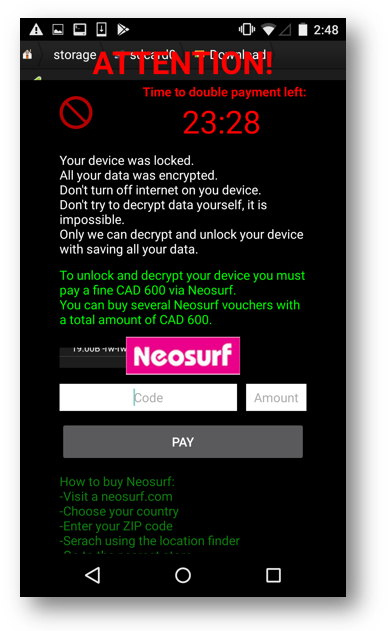
After a couple of minutes we get a ransom message that covers the entire screen as shown below:
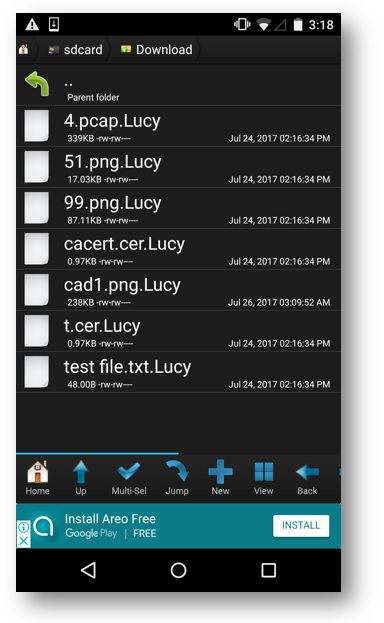
In the background the ransomware encrypts files on the device and adds a ".Lucy" extension at the end
This ransomware demands the victims to pay 600 Canadian Dollars (CAD) which amounts to roughly $481 at the time of writing this blog. The attackers demand payment via Neosurf - wherein we purchase a Neosurf voucher of a certain value using cash. To fulfill the payment the victim needs to add the voucher number or code.
Additional points
- The malware contains the following hardcoded urls in its code:
- hxxp://fsdf2tvwev-ru.1gb.ru/private/add_log.php
- hxxp://fsdf2tvwev-ru.1gb.ru/private/reg.php
- hxxp://fsdf2tvwev-ru.1gb.ru/private/set_data.php
- Since its discovery, statistics on the above URLs indicate most of the clicks/visits for these links have been coming from Canada indicating where this ransomware might have spread the most
- There is a hardcoded phone number present in the code +190 which belongs to the United States
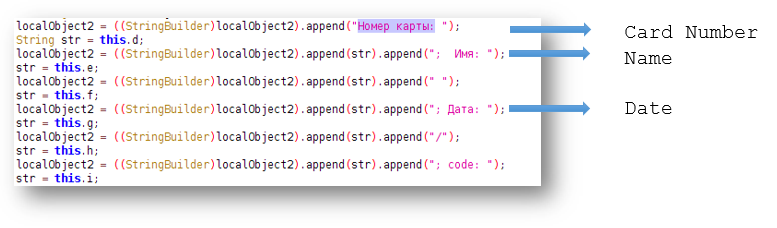
- We observed code that looks for a card number, name and date. This code might be for Neocash which is a CreditCard by Neosurf:
- There is code in the ransomware that extracts the contact details stored on the device:
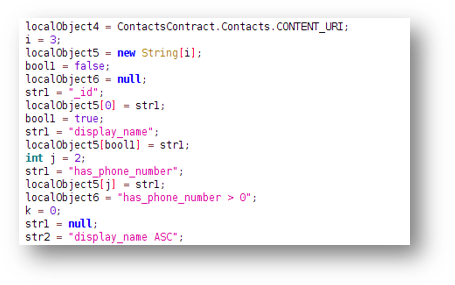
- This ransomware has the ability to execute commands received by the attacker, few interesting ones are listed below:
- Execute shell commands
- Grab SMS messages on the device
- Compose and send SMS messages
- Get location of the device
The ransomware gets installed on a device as a codec pack, based on its name it is likely that this is spreading via rogue websites that host a video but show an error when the user tries to play the content. The error usually claims that a codec pack is missing on the device and the video will play once the codec is installed.
We urge our readers to please be aware when such an error is encountered, it is always advisable to install apps on the device via the official Google Play store and not directly from websites.
SonicWALL provides protection against this threat via the following signature:
- GAV: AndroidOS.Ransomware.CAD (Trojan)
The following sample was analyzed for this blog:
- MD5: 615869b81f1ccdbdbb1fa338744c0a6d
- Package: com.android
Share This Article

An Article By
An Article By
Security News
Security News