Android PornDroid ransomware with updated features (September 25, 2015)

After the surge in attacks from encryption-based threats like CryptoLocker and Cryptowall, malware attacks that restrict access to a system have grown in numbers. These attacks have targeted both PC and Android ecosystems alike. LockDroid/PornDroid is a ransomware for Android that has been present since late 2014 and over time it has undergone a lot of changes.
Dell SonicWALL Threats Research team observed a new variant on the rise that adds a new component to the Android ransomware scene. In addition to the lockscreen that renders the infected mobile device unusable, this malware adds a PIN based Android lockscreen thereby preventing the user from unlocking the device. Even though the PIN is random, the attackers demand $500 as a ransom for unlocking the device and removing the lockscreen.
Infection Cycle
The malware requests for following permissions during installation:
- Camera
- Get tasks
- Get accounts
- System alert window
- Access wifi state
- Change wifi state
- Change network state
- Write settings
- Kill background processes
- Read contacts
- Receive boot completed
- Read phone state
- Internet
- Wake lock
- Access network state
- Read browser history
- Read browser bookmarks
Once installed, the app requests for Device Administrator privileges when it is clicked. With device administrator privileges an app can perform privileged tasks like erasing data or resetting lockscreen password on the device :
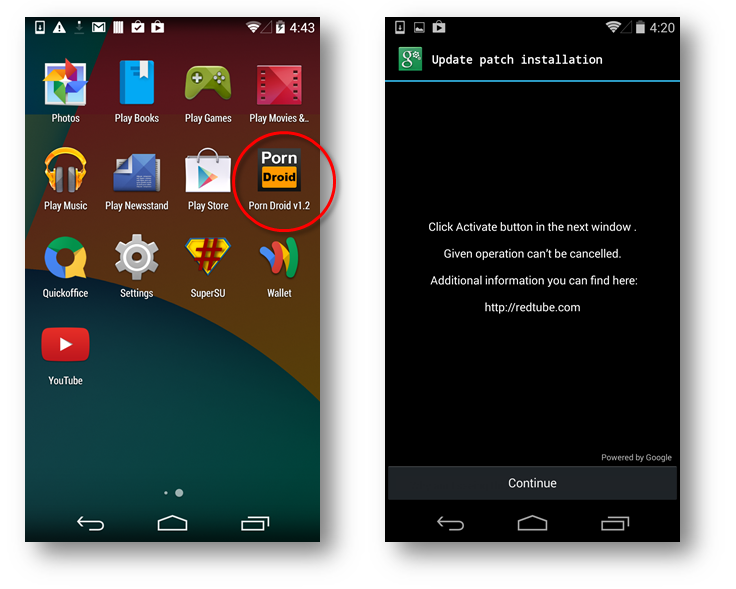
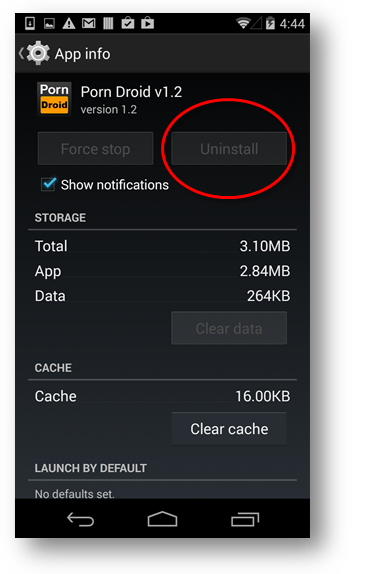
Granting Administrator Privileges also makes it difficult to remove said apps as the uninstall button turns un-clickable:
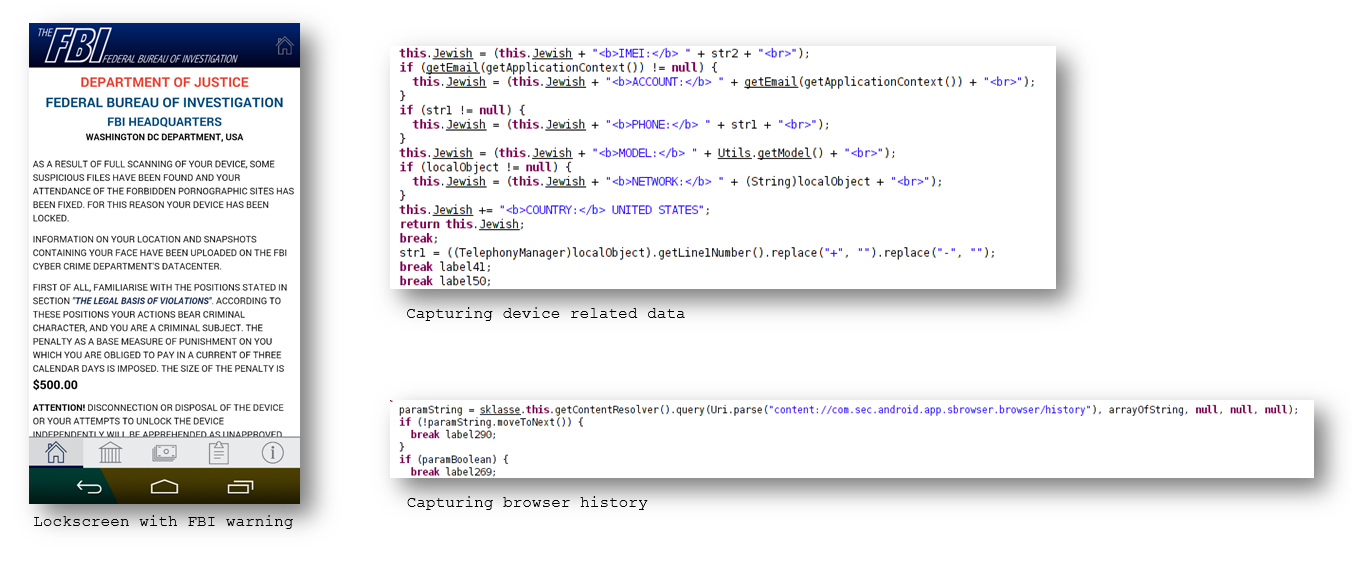
The malware then shows a lockscreen with FBI (Federal Bureau of Investigation) warning message thereby disabling general usability of the mobile device as all the control buttons are superceded by this lockscreen. In the background the malware starts to gather a suite of information from the device which is later used on the lockscreen making the lockscreen more "personal" for the user. The following are a few key pieces of data that are gathered:
- Phone model Number
- Network Operator
- Country
- There is code in place to take a picture from the device camera
- Browser history
- Browser Bookmarks
At the time of writing this blog the server to which this malware communicates to is down, we could not see the dynamic lockscreen containing the above mentioned data elements.
The malware tries to communicate with the following domain:
- onlyfor18.org
It has the following Command and Control (C&C) related hardcoded data:
- Server: facebook-tw.zp.ua
- Panel: /delopnaktis/bloqyxpn.php
Lockscreen malware for Android have been a common occurence in the recent past, one such lockscreen malware by the name LockDroid/PornDroid has seen a number of changes and enhancements since its first discovery. The malware being analyzed is a new variant of this family and the following are few key similarities and differences with regards to the different versions:
- The FBI warning message on the lockscreen is identical in the variants
- We saw the domain onlyfor18.org in most of the variants
- The server and panel domains vary slightly in the variants
- hxxp://facebook-tw.zp.ua/pafumokat/bloqyxpn.php
- hxxp://facebook-tw.zp.ua/delopnaktis/bloqyxpn.php
- The string sklasse is present in all the variants in some form
- A major upgrade in the most recent verions relates to how code is obfuscated in order to thwart Security Analysts and automated Static Analysis tools:
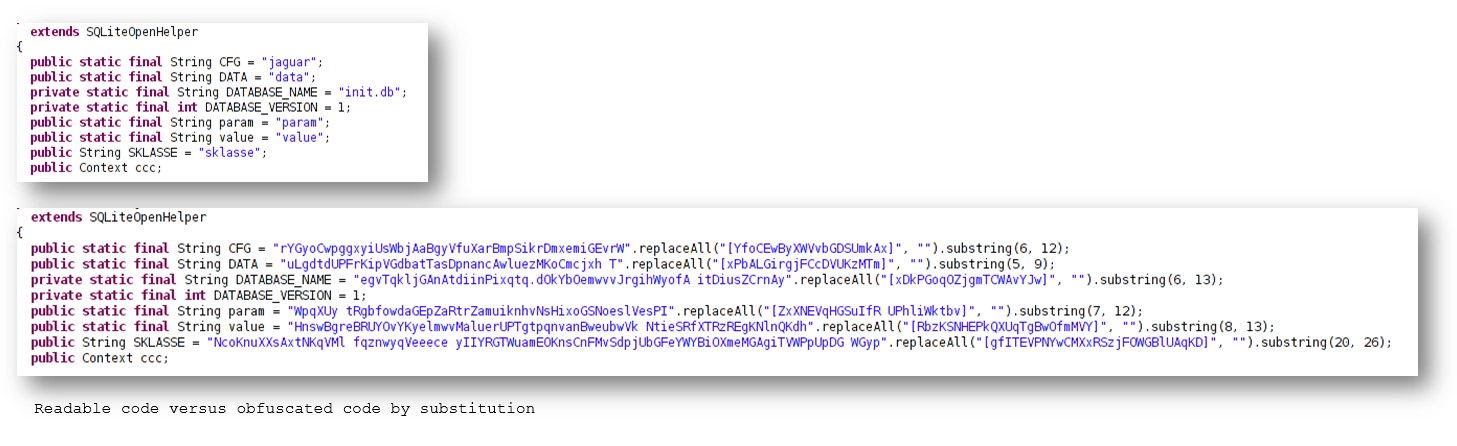
- Older verions have a clean readable code, some of the new versions have code where readable text is mixed with unwanted characters that are later removed as needed:
- The level of obfuscation in the code using this substitution technique varies over multiple variants
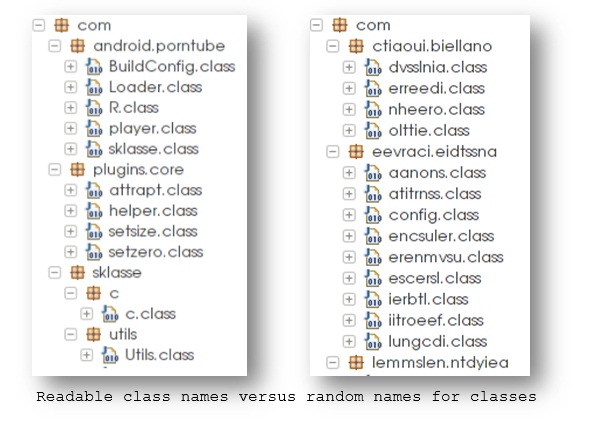
- Some variants have readable class names whereas some have random-looking names:
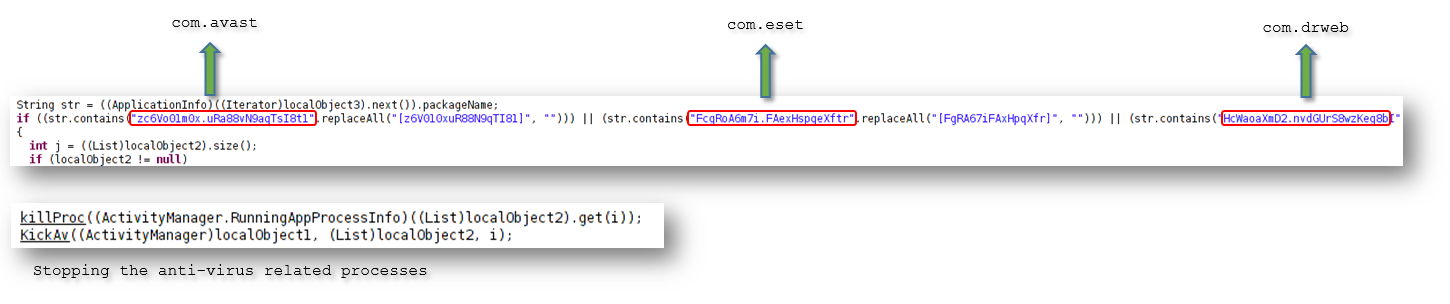
- Most of the recent versions detect if certain Anti-Virus solutions are running on the device, if so, they are stopped:
- Older verions have a clean readable code, some of the new versions have code where readable text is mixed with unwanted characters that are later removed as needed:
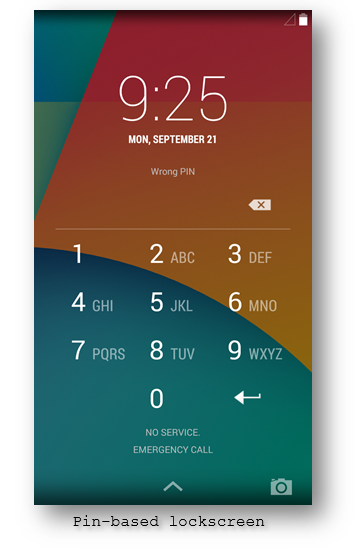
- Another major addition in the new variant relates to the actual phone lockscreen. As part of the device security mechanism Android users can improve security on the phone by setting up a lockscreen password when the phone is unlocked. This is mainly to avoid strangers from unlocking the device. This malware upon infection sets its own screen lock password thereby adding another lockscreen over the already existing (FBI warning) one:
The main aim of LockDroid/PornDroid is to extract ransom from the victims of infected devices, it has been evolving over time with new components that hinder its detection/analysis. We can expect more developments in future that would improve the damage caused by this threat and at the same time make it laborious to analyze and detect it easily.
Few safe and potent ways to avoid getting infected from this threat are:
- Download and install apps exclusively from the official Google Play store
- Grant Administrator privileges to trusted apps only
- Be aware of the risks of Rooting your device
Dell SonicWALL provides protection against multiple versions of this threat via the following signatures:
- GAV: AndroidOS.Locker.IC (Trojan)
- GAV: AndroidOS.Locker.FBI (Trojan)
- GAV: AndroidOS.Locker.PornDroid.V1 (Trojan)
- GAV: AndroidOS.Locker.PornDroid.V2 (Trojan)
- GAV: AndroidOS.Locker.PornDroid.V2_2 (Trojan)
APK Package Details:
- Package Name: com.android.porntube
- MD5: 4b4d8abbca536c987fca430af62c9bc8
- Package Name: com.lemmslen.ntdyiea
- MD5: 82990aad8c1a1894d7b7fd56e78c3a6b
- Package Name: com.tartiap.lnnhdatu
- MD5: 187f7d5ae06b386581f5f177340ca2b7
- Package Name: fpgb.xpgbuoz.exug
- MD5: f65657f31da966e1a4f52488f91d9e90
- Package Name: dwag.jvykqfj.brgnx
- MD5: d7fffb1934fd8abf88a4e6a4c1d06a7a
Share This Article

An Article By
An Article By
Security News
Security News